As a follow-up to my recent posts about a suspect using CCleaner in an attempt to hide their Internet activity, I received several emails asking about Internet Evidence Finder’s ability to recover InPrivate browser artifacts that I wanted to address.
Here is the link to Part one and Part two of my original CCleaner posts as well as a video Jad shot a while back explaining some of the behaviors of ‘InPrivate’ Browsing and the artifacts left behind.
InPrivate Browsing is a feature of Internet Explorer that was first introduced in IE version 8, beta 2 (August 2008). InPrivate is really several features, with the most common being known as ‘porn mode’ which is designed to allow the user to browse the Internet without the browser storing Internet history and webpage cache information, as it typically does. This feature was really designed for public computers where traditionally without the use of “InPrivate” a person’s browser history could be viewed by anyone else who has access to that user account profile. For example, an Internet café, where a user rents a computer for a time period and then a subsequent user, could view the history and view the cached data that was stored on disk during the previous user’s browser activity.
A description of InPrivate on an IE8 wiki page states:
“InPrivate Browsing in Internet Explorer 8 helps prevent one’s browsing history, temporary Internet files, form data, cookies, and usernames and passwords from being retained by the browser, leaving no easily accessible evidence of browsing or search history. InPrivate Filtering provides users an added level of control and choice about the information that third party websites can use to track browsing activity. InPrivate Subscriptions allow you to augment the capability of InPrivate Blocking by subscribing to lists of websites to block or allow.
“As with other private browsing modes there are ways that information about a browsing session can be recovered.”
I highlighted two parts of the description that are very accurate and important. The first is that InPrivate mode was not designed as anti-forensics. It was intended to provide some privacy features so that the user’s browsing activity could not be easily accessible. The use of “easily accessible” does not apply to digital forensics. The second is the disclaimer that there may be ways to recover the browser activity that was generated during an InPrivate session.
InPrivate mode is activated in Internet Explorer by selecting Tools-> InPrivate Browsing (Ctrl+Shift+P). Depending on the version of IE, the word “InPrivate” will appear either in the title bar or address bar, as shown below. Any links or action that opens/spawns additional tabs will also be “InPrivate” mode.
InPrivate mode may not be exactly what you were expecting. As forensic examiners, we sometimes expect a feature that advertises itself with the goal of protecting a user’s privacy to also hinder us during a forensic examination. The reality of InPrivate mode is that Internet Explorer actually still creates data on the disk related to the user’s browsing activity. Cached files are still placed in the typical “Temporary Internet Files” subdirectories, and although the user’s history is not visible from the Internet Explorer UI, URLs are still recorded in the index.dat file(s).
When IE is closed, the files that were cached on the filesystem are then deleted (not wiped). In addition, many (if not all) of the artifacts that were generated by the user’s browser session were at some point in memory and ultimately make their way to the pagefile, which InPrivate mode has zero effect on.
To demonstrate this, I installed Windows 7 from the original installation media. With zero web browsing history after the installation, I immediately entered InPrivate mode and browsed to Facebook, Gmail and Yahoo Mail.
Here is an example of the files created on the file system during an InPrivate session (note the path):
When the browser was closed, the above files were deleted and the folder was left with only a few files:
A forensics look after IE was closed and a reboot reveals this:
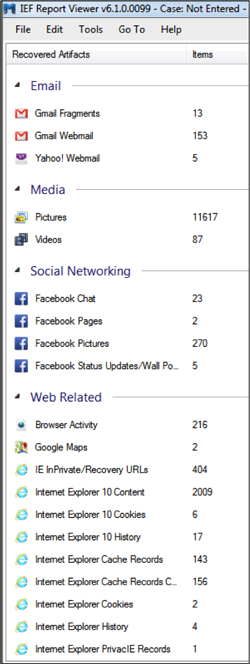
A quick scan with Internet Evidence Finder reveals tons of artifacts, many of them in the pagefile and unallocated:
So, does Internet Explorer ‘InPrivate’ mode do what it’s supposed to? Sure, it does conceal a user’s browser history from UI and common tools, pretty much as advertised.
Does it pose a severe threat to forensics? Not so much…
There are a couple of very important factors that can affect your outcome and your mileage may vary based on these factors:
- Collection of RAM!, Collection of RAM!, Collection of RAM!
- The time period between the InPrivate session being closed and the forensic examination (since data is now in unallocated).
- The amount of new file system activity between the InPrivate browser session and the forensic examination, since this will affect how long the data in unallocated remains without being overwritten.
- The amount of memory usage/activity between the InPrivate browser session and the forensic examination, since this will affect the pagefile.
As always, I appreciate the feedback, comments or questions.
You can reach me anytime at lance (at) magnetforensics.com