For the last few years now, most forensic examinations of iOS devices were limited to data only available in an iTunes backup and only if you had the user’s passcode. Sure, you may have gotten the odd jailbroken device, but it typically didn’t matter whether you had a ten thousand-dollar commercial forensics tool or a free acquisition tool like Magnet ACQUIRE, you were getting the same thing, an iTunes backup / logical collection of files. If you didn’t have the user’s passcode, you weren’t getting anything, so a backup was better than nothing.
Enter Grayshift, the makers of GrayKey, a tool which allows law enforcement to crack the user’s passcode, bypassing the Data Protection delay and gaining access to the entire file system of iOS devices. This not only has provided examiners with access to devices that were previously inaccessible due to not having the passcode, but also gave them access to iOS data that hasn’t been available in years due to the limited data available via logical collections. In some cases, GrayKey revealed data we’ve never had the opportunity to investigate before as well!
As many know, GrayKey is only an acquisition tool, meaning it will allow examiners to gain entry into iOS devices, and makes extractions of the information found, but it doesn’t assist with any analysis. Data acquired via a GrayKey extraction is outputted into a variety of zip containers (BFU, AFU, Full Files, mem, and a keychain.plist. Magnet AXIOM can then be used for analysis of these files.
Clik here to view.
For investigators, the ideal GrayKey image you want when examining an iOS device is the files.zip. This has the entire iOS file system present and provides the maximum amount of information for examiners to use in the course of their examination. While the other available image types provide great forensic value for case work, when available always exam the files.zip image first.
Your GrayKey will also produce a passwords.txt and a HTML report of the device extraction. While the passwords.txt list is great for examiners to look through, make sure to load the keychain.plist into AXIOM for parsing, not the passwords.txt file.
Keep in Mind: Even if you have the user’s passcode, still utilize the GrayKey for the extraction, so that you have as much data as possible to work with for your investigation.
The next container is mem.zip. This is a process memory dump of the iOS device. Prior to Grayshift’s technology, examiners hadn’t acquired process memory of iOS devices for routine analysis. Memory acquisition on Android can be done but as it requires a phone restart, the investigative value is minimal. In this case, the iOS process memory contains valuable information and should most certainly be loaded into AXIOM as well.
Finally, the last file is the keychain.plist. Most examiners are familiar with the iOS keychain as it contains the user accounts, passwords, and keys for many of the apps that the user has saved or used which can also be valuable for investigators wanting to authenticate to cloud sources or otherwise. The keychain that GrayKey creates is slightly different than the one you would get in an iTunes backup or found natively on a jailbroken device. The keychain found in the file system is actually a SQLite database and hasn’t always been available due to limitations in acquisitions prior to this. The keychain in an iTunes backup is also a plist but is formatted differently so we’ve added specific support for the GrayKey keychain.plist in AXIOM.
Clik here to view.
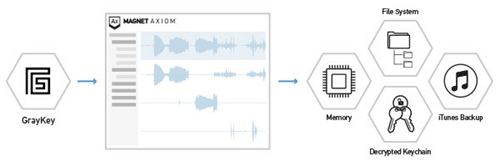
Now that we’ve highlighted different exports examiners get from utilizing a GrayKey in their acquisition phase of their iOS investigation, let’s dive into analyzing this data with Magnet AXIOM.
Loading GrayKey Evidence into AXIOM
There are several ways to load your recently acquired iOS device into AXIOM. Depending on the needs of your investigation, you may find one method better than others for your workflow.
To start, instead of loading your files.zip file you’ve acquired, I’d first recommend loading the keychain.plist in via:
Clik here to view.
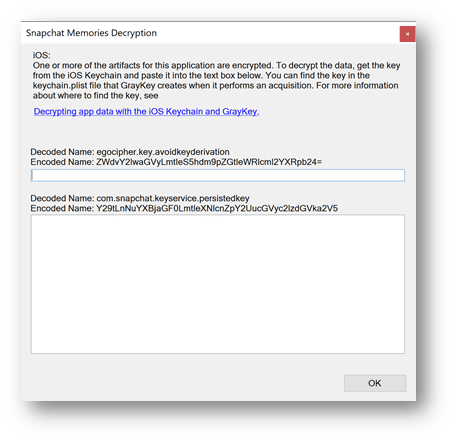
One of the great benefits of using AXIOM for your analysis is the ability to add in multiple pieces of evidence all at the same time before processing begins, saving investigators time. That being said, when dealing with iOS devices that you have the keychain.plist for, it’s beneficial for the examiner to process the just the keychain and to review the data of that sole piece of evidence before navigating to the Case Dashboard of AXIOM Examine and hitting “Add Evidence”. Why you ask? Great question! If an examiner has already reviewed the keychain.plist, they will have a good idea of the apps that may be found on the suspect device. Better yet, when they load the files.zip into AXIOM for processing, they can supply potential passwords and key values for encrypted apps like SnapChat, WickrMe, or iOS Notes, so that during processing AXIOM can decrypt these databases for the examiner to analyze during the course of their investigation, without the need of having to re-process the evidence. We’ve added information within the artifact selection category for apps that we can decrypt during processing for examiners to reference when copying information out of the keychain into AXIOM, as seen below.
Clik here to view.
Next let’s look at loading in additional GrayKey evidence files into AXIOM.
Clik here to view.
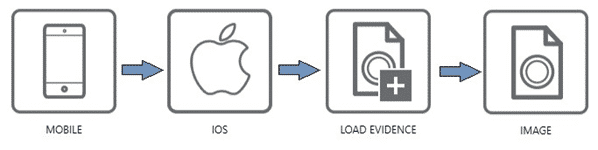
To load GrayKey images into AXIOM, you can follow the same path as most other iOS images by going Mobile -> iOS -> Load Evidence -> Image and then choosing the files.zip first. Next, load the mem.zip in the same manner.
It’s important to note, make sure you select “Image” versus file and folder when loading in the files.zip. This will allow AXIOM to parse / carve the maximum amount of information out of the image.
Clik here to view.
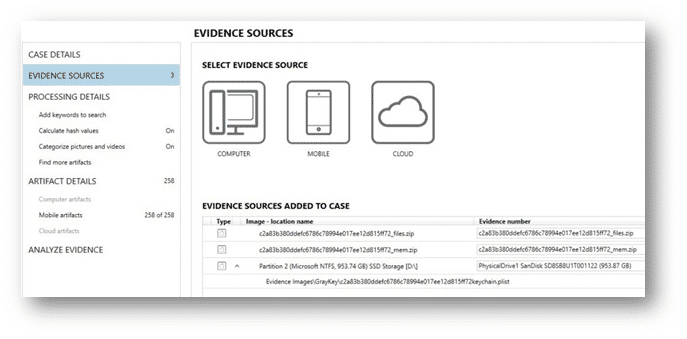
For agencies with an online GrayKey there is an additional option when it comes to loading your acquisitions into AXIOM. In conjunction with Magnet’s exclusive partnership with Grayshift, we have a direct connection which allows examiners to connect AXIOM directly to their GrayKey via a network connection. This direct-connect option has several benefits over the traditional procedure of downloading the images via a browser from your GrayKey before starting a case with your analysis software. The first benefit of using the direct connect option is speed; using this procedure reduces the steps needed to start your investigation overall, and when it comes to the volume of iOS devices you’ve acquiring, this time savings can really mount up. Secondly, AXIOM will prompt you on where to save the GrayKey image too as its acquired and processed for examination. As a part of this process we will also automatically hash the files we are acquiring, so that you can quickly confirm from the GrayKey GUI your hash values match. On numerous occasions we’ve heard investigators say that when they loaded their GrayKey image into their analysis tool, things seemed “off”, or the image couldn’t be loaded. This is in part to potentially the browser capping the size of the download, or a packet dropping during the download of the image file.
Clik here to view.
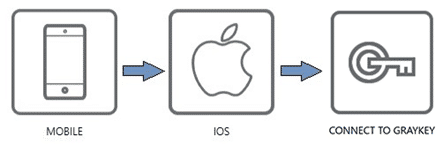
To load evidence via the direct connect method, users will go Mobile -> iOS -> Connect to GrayKey. Once connected, examiners can browser the available data that’s saved on the GrayKey, selecting the different evidence files they wish to acquire and process with AXIOM.
Once loaded you can choose whatever options and artifacts you wish to include in AXIOM for your given investigation. One feature that may help get additional data that otherwise wouldn’t be included in an artifact is the Dynamic App Finder (DAF).
Clik here to view.
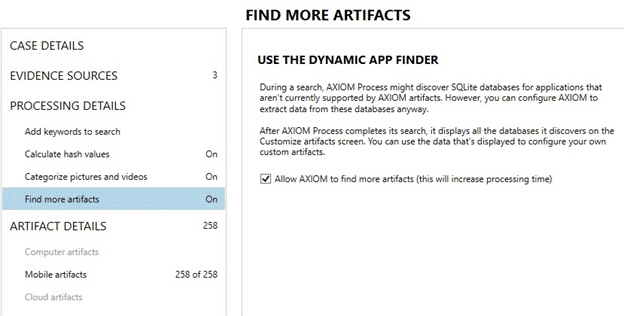
Under “Find more artifacts”, you can enable DAF and it will automatically search through the image for SQLite databases that may contain potential chat, geolocation, or contact information. This can be helpful for any applications or data that can’t already be found in an existing artifact. A quick video on DAF can be found here. For GrayKey images, this will identify additional data in the file system and memory images. You can find more information on creating custom artifacts and learning more about our Artifact Exchange here.
Once everything is loaded and options are selected, you can process the case just like any other and view the results in AXIOM Examine.
Clik here to view.
Want to learn even more about how you can use GrayKey and AXIOM together to maximize your iOS investigations? Check out our MAGaK (Magnet AXIOM & GrayKey) Advanced iOS Examinations (AX301) course!
The post Loading GrayKey Images into Magnet AXIOM appeared first on Magnet Forensics.