April 23-25, 2013
Las Vegas, Nevada
AccessData User Conference (ADUC)
International Communications Data & Digital Forensics Seminars 2013 (ICDDF)
March 18-21, 2013
United Kingdom
US Defense Cyber Crime Institute (DCCI) validates Internet Evidence Finder (IEF)

We are pleased to announce that Internet Evidence Finder (IEF) v5.8 has been validated by the United States Defense Cyber Crime Institute (DCCI). DCCI is the research, development and evaluation arm that tests tools tailored to the specific requirements of digital forensic examiners and cyber intrusion analysts. DCCI is a part of the Department of Defense Cyber Crime Center (DC3).
Our law enforcement customers are always interested in 3rd party reviews and examples of how IEF can be used in their digital investigations. The validation from DCCI falls on the heels of a positive review of IEF on ForensicFocus.com, as well as a favorable evaluation report from the National Institute of Justice’s Electronic Crime Technology Center of Excellence. Having IEF validated by the US DCCI is another big vote of confidence for our team. We hold ourselves to an incredibly high standard, and pride ourselves on developing quality products that deliver accurate results. It’s great to have external validation that we are on the right track.
The DCCI report evaluated IEF on 26 different criteria to determine the circumstances under which computer crime investigating agents assigned to Defense Criminal Investigative Organizations (DCIOs) may employ IEF for digital forensic investigation and analysis.
Findings included:
- IEF is forensically sound and does not modify evidence files upon reading them
- IEF successfully produces the same results after being run against the same dataset multiple times
- IEF successfully recovered data from a number of Internet related artifacts including: Hotmail, SkyDrive, Skype, Yahoo, AOL, Facebook, Gmail, Google Documents, Limewire, Dropbox, Twitter and more
- Examiners have the ability to search a dataset created from a RAM capture using IEF
Unfortunately, we aren’t perfect and there were 3 artifacts that DCCI identified in their report as not satisfying their criteria. With the generous help of the staff at DCCI we were able to fix 1 of them right away and they will be available in v6 later this month. The other two artifacts are new updates/new versions of the supported artifacts and will go into a point release (6.x) in early Q2 of this year.
The DCCI report is available to U.S. federal, state, and local law enforcement agencies, and law enforcement officials from Australia, Canada, England, & New Zealand. To download the report users can go to https://dfilink.net/ .
Our thanks go out to the DCCI and DC3 folks for selecting IEF to go through this rigorous validation process.
We appreciate your support!
- Jad and the Magnet Team
Internet Evidence Finder Adds Mac OS X File System Support & New Timeline Feature in Latest Upgrade to Forensic Software
With a strong commitment to helping thousands of its customers in the world’s top law enforcement, military, government and corporate organizations recover data from a broad range of Internet-related communications, Magnet Forensics (formerly JADsoftware) has launched v6.0 of its industry-leading forensic software, INTERNET EVIDENCE FINDER™ (IEF).

New features include:
- Mac OS X File System Support
- Import and process forensic images acquired from volumes and virtual machines formatted with the HFS+ and HFSX file systems
- Carving & Parsing of Mac images, including:
- Popular social networking sites, instant messenger chats, webmail, P2P file sharing apps, web browser history, pictures & videos, iOS backups and cloud artifacts
- Unique Mac artifacts supported include: iChat, Adium and Amule
- Mac “Time Machine” backup application
- Sleep Image – hibernation file (when not encrypted/compressed)
- Swap File (when not encrypted)
- Rebuild Safari webpages as they were originally viewed by the computer user
- IEF Timeline Feature
- View results in a graphical timeline with the ability to import .tln files
- Drill down to isolate webmail, chat messages, browser history and more during a specific time-frame
- Zero-in on specific dates in time, or spikes in a suspect’s online activity
- Improved Image Search Stability and Support
- Native Image support for: E01, Ex01, L01, Lx01, dd and dmg format (no mounting)
- Virtual machine image support: vmdk, vhd, vdi and xva
- Faster Search Capabilities
- Now offers multi-threaded support for multi-core processors
- Searches run 2-3 times faster on a quad-core CPU
- New Artifacts & HTML carving
- 360 Safe browser, QQ Chat, Bing Toolbar, Google Toolbar, Bing Maps, Bing Search History, Xbox IE History, Limerunner, Luckywire, and enhanced Limewire/Frostwire and Gigatribe support
- Webpage recovery/HTML carving for Craigslist Ads, Backpage Ads, Ashley Madison and Plenty of Fish
IEF software mainstays include:
- Powerful Search Capabilities: Single search for 220+ Internet artifacts
- Find Evidence Quickly: Get immediate search results, work with found data right away
- Simple to Use: Get to key evidence in 3 easy steps
- Comprehensive Reporting: Create standardized and straightforward reports
- Built-in Intelligence: Web Page Rebuilding and more
- Adheres to Industry Standards: Maintain the integrity of the case, and chain of custody
Learn More:
- Watch our IEF v6.0 Getting Started Walk-Through Video, or IEF Timeline Feature Video
- Visit our IEF Product Page for more info
- Register for an IEF Webinar
Pricing/Availability
IEF v6.0 is available today starting at $999 USD.
Existing customers with a Software Maintenance & Support (SMS) subscription can upgrade to IEF v6.0 for free by visiting our customer portal.
Customers without an SMS subscription can email sales@magnetforensics.com or call 519-342-0195 for pricing.
To download a FREE 14-day free trial of IEF v6.0, please click here.
About Magnet Forensics
Magnet Forensics (formerly JADsoftware) is a global leader in the development of forensic software that recovers data from a broad range of Internet-related communications. Our flagship product, INTERNET EVIDENCE FINDER™ (IEF) was created by a former police officer and forensic examiner who recognized the need for an easy to use, comprehensive tool to help perform digital investigations. Since its creation, IEF has quickly become a trusted solution for thousands of the world’s top law enforcement, government, military and corporate organizations – used to recover Internet evidence like social media communications, webmail, browser activity (and more) to support their most important investigations.
IEF v6 taking computer forensics to the next level!
The team has been working hard over the past several months on the architecture of IEF to leverage multi-core processors, support Mac file systems, and add more visualization. Everyone at Magnet is very excited to be releasing Version 6 of IEF! We are continuing to push the boundaries and have some very exciting things coming with v6.1 that will make IEF a must have tool for every forensic examiner on the planet.
Last year was busy as we iterated on v5, with our last release including features like Dropbox decryption support, Google Maps tile recovery, web video fragment recovery, and other useful artifacts/features.
Let me take a minute to highlight some of the features I’m really excited to be bringing to our customers in v6.
Mac OS X file system support: Previous versions of IEF did not support file systems other than NTFS/FAT and so with Mac images you were limited to a sector-level search. Now IEF natively parses images (no mounting or drivers required) and can parse HFS/HFS+ file systems along with Windows file systems. This allows for more control over which areas of the drive are searched, more information around where artifacts are found, and better handling of files that are fragmented or containing data that is not easy to carve. We’ve also added more support for Mac specific artifacts, including Safari webpage rebuilding, Adium chat, iChat, and Amule. This is just the beginning with our Mac support and we will continue to add new artifacts based on customer requests and market trends.
Timeline feature: This new feature has been in development for some time now and we’re excited to reveal it. IEF Timeline will display recovered artifacts visually allowing you to see spikes in a user’s online activity, or the absence of activity. You can drill-down to specific time frames and isolate certain artifacts that are of interest. It really needs to be seen to appreciate the investigative value that it can bring to your examinations. You can also import/export .TLN files which allows for sharing of data between forensic products. Click here to see a short video.
Virtual Machine image support: IEF now natively supports .vmdk, .vdi, .vhd, and .xva image files, along with the standard forensic image formats: .E01/Ex01, .L01/Lx01, dd/001.
Multithreading: Tired of seeing forensic products use only one of your 32 CPU cores? Now IEF can take advantage of multi-core CPUs, resulting in very large speed increases.
New Artifacts: A number of new artifacts have been added or improved in v6. Some of the notables include: 360 Safe browser (a Chinese browser that is essentially a mash-up of IE and Chrome), QQ Chat (popular Chinese chat program with over 712M active users), Bing & Google Toolbars, Xbox360 Internet Explorer History (a forensic first!), and enhanced Limewire/Frostwire/Limerunner/Luckywire and Gigatribe support.
We’ve also added a sophisticated HTML carving engine that can recover web page fragments from Craigslist, Backpage, Plenty of Fish, and Ashley Madison websites. This new engine will allow us to continue to add web page fragment recovery for other popular sites that regularly find their way into investigations.
If you are already an IEF user, please upgrade via the Customer Portal or use the inline updater now available with IEF. To download a trial of IEF, please click here.
Finally, we are proud to announce that Internet Evidence Finder has been nominated for the Forensic4cast
“Computer Forensic Software of the Year” award! Our thanks go out to all those who nominated us.
Thanks for your continued support!
Jad and the Magnet Team
Industry Veteran & Thought Leader Lance Mueller Joins Magnet Forensics Team

With a strong commitment to helping thousands of its customers in the world’s top law enforcement, military, government and corporate organizations recover data from a broad range of Internet-related communications, Magnet Forensics (formerly JADsoftware) has brought industry veteran and thought leader, Lance Mueller onto its growing team as Director of Forensics.
With a successful career in Law Enforcement and forensics spanning 24 years, Mueller spent his first 14 in LE; including a 5-year stint investigating high-tech crimes as a DA investigator assigned to California’s Computer and Technology Crime High-Tech Response team (CATCH). With CATCH, Mueller was lead investigator on a number of high-profile cases, including a global hacking case where the suspects were jailed for helping create a virus that affected thousands of computers globally: http://news.bbc.co.uk/2/hi/uk_news/england/4319942.stm. The case was also highlighted in Malicious Bots – An inside look into the Cyber-Criminal Underground of the Internet – a book Mueller contributed to.
In 2003, Mueller left Law Enforcement for a position with Guidance Software as a Master Instructor and trainer for law enforcement, military, government and corporate examiners. While there, he developed several of the training courses that are still in use by the company. Mueller then transitioned to Guidance’s professional services division where he conducted incident response and forensic examinations for many of their Fortune 500 clients.
Mueller then took a position with the US Department of State Antiterrorism Assistance (ATA) program in 2005, traveling to multiple countries to teach digital forensics best practices, setting up computer forensics laboratories and conducting forensic capability assessments.
For the last two years, Mueller has worked at Qualcomm as a member of their global security team, responsible for conducting incident response, digital forensics and world-wide investigations. He also maintains a popular forensics blog: www.ForensicKB.com.
As Director of Forensics at Magnet Forensics, Mueller will work closely with Founder & CTO, Jad Saliba to provide feedback and ideas on useful features that forensics examiners can leverage to assist in completing their cases quickly and efficiently. Mueller will also assist in identifying and conducting research on emerging artifacts that could be integrated into IEF, and develop specialized training for IEF users. He will also contribute regularly to the Magnet Forensics blog, and write articles, whitepapers and tip sheets for the forensics community that will be posted on the website.
About Magnet Forensics
Magnet Forensics (formerly JADsoftware) is a global leader in the development of forensic software that recovers data from a broad range of Internet-related communications. Our flagship product, INTERNET EVIDENCE FINDER™ (IEF) was created by a former police officer and forensic examiner who recognized the need for an easy to use, comprehensive tool to help perform digital investigations. Since its creation, IEF has quickly become a trusted solution for thousands of the world’s top law enforcement, government, military and corporate organizations – used to recover Internet evidence like social media communications, webmail, browser activity (and more) to support their most important investigations.

Learn how Internet Evidence Finder (IEF) complements EnCase and/or FTK
I thought I would spend some time explaining how Internet Evidence Finder (IEF) can complement the investment you have made in EnCase and/or FTK . The world of forensics has certainly changed over the past 5 years with much more evidence being found in Internet-related artifacts like Facebook, Twitter, Gmail, Skype, Google Talk, Yahoo Messenger and many others. In addition, the way we use computers has changed over the past few years with “always-on” broadband connections being ubiquitous. More and more daily tasks and communications are happening in the “cloud”. This has caused Internet–related artifacts to become an essential part of every investigation.
The myriad and continually changing ways to share information via social media has resulted in a goldmine of potential evidence: profiles, lists of friends, group memberships, messages, chat logs, tweets, photos, videos, tags, GPS locations, check-ins, login timetables and more.
We have consolidated what we believe are the top 5 reasons to consider putting IEF into your toolbox to complement EnCase and FTK .
- Save precious time by getting to the evidence quickly. IEF is a targeted single search that gives you the ability to search all 220 artifacts in a few easy steps. IEF does all the heavy lifting for you and recovers the Internet-related data without any manual intervention. You can get up and running in less than 1 minute and the data starts populating in the report viewer in real-time. Just “Set it and forget it”.
![Search Status Computer dialog showing search results]()
For example, we ran a Full search with Internet Evidence Finder (IEF) on a computer with the following specs: Intel i7-3770 3.80GHz CPU (4 cores, 8 logical processors), 16GB RAM, 2TB Seagate 7200rpm SATA drive (contained the evidence files), Windows 8 64bit OS. It took 4 hours, 4 minutes, and 44 seconds and recovered 122,985 Internet related artifacts. The search summary is pictured above. - Dead simple to use.IEF takes the need of having an extensive forensics background out of the equation. The operator only needs to answer a few simple questions that do not require deep technical knowledge.
Only 3 steps and you are recovering the evidence. First pick your drive or image, then select the artifacts to search for, and then view the results in a standardized report. The learning curve is very minimal and you don’t need extensive training to feel confident in using the product.
Point it at the drive, file/folder, or forensic image.
![IEF Main Screen Point it at the drive, file/folder, or forensic image]()
Select which Internet artifacts to search for. They are all checked by default.
![Select internet artifacts to search for Select which Internet artifacts to search for. They are all checked by default.]()
Click “FIND EVIDENCE” and the results start populating the report viewer in real-time.
![Find Evidence Screen shot of results starting to populate the report viewer]()
- Tools to make it easier to find the key evidence. IEF can rebuild webpages into their original form which is often critical in court for a jury or judge. Other capabilities include pulling out the search engine keywords the subject used on the major search engines. In addition, IEF can refine picture results by skin tone, categorize visited URLs, and decode Facebook URLs.
![Refined Results List of IEF refined search results]()
- Standardized reporting that’s easy to understand and explain. IEF will produce a well-documented report in all the common formats every time. Easily create a report in pdf, excel, html, csv, tab-delimited formats, or create a portable case and share it with others like prosecutors that don’t have IEF.
![Standardized reporting that easy to understand and explain A simple to read results report]()
- Find evidence that you didn’t know was there. IEF can recover over 220 Internet-related artifacts including social networking sites, webmail, cloud artifacts, instant messaging history, web browser history (including private browsing), P2P file sharing apps, iOS backups, and pictures & videos. IEF’s search algorithm was purpose built for recovering data from today’s Internet communication sites and applications. Our expertise is in the recovery of Internet-related artifacts and keeping up with the constant changes of these Internet artifacts. It doesn’t matter if the artifacts are in unallocated space or where they normally logically exist, IEF will make it as simple as possible and grab all the artifacts it can find no matter where they are.
If you have any questions about IEF or want to give it a try please contact us at sales@magnetforensics.com
IEF has been nominated for the Forensic4cast “Computer Forensic Software of the Year” and we would love your vote.
Thanks for your continued support!
Jad and the Magnet Team

Why I use IEF. The simple answer is efficiency.
Well, it’s day two for me at Magnet Forensics and I thought I would take the opportunity to say “hello” to everyone and briefly comment on why I chose to work here and why IEF has been a “go to tool” in my toolkit for a while now.
Magnet Forensics is a very unique “family” business. Nobody is technically related, but everyone treats each other like family and it is one of the most positive goal-oriented teams I have ever worked with. Everyone in the company has a genuine interest in producing tools that are not only very useful and functional, but also serve the greater good of helping the good guys beat the bad guys (Jad has taught them well ![]() ).
).
I also thought it might be relevant to explain why I chose to use IEF during investigations in the past. Since its day two for me at Magnet Forensics, my hope is that this message comes across as an impartial forensic examiner still and not as a Kool-Aid drinking employee of Magnet Forensics (it’s too early yet ![]() ). For those of you who know me, you know I am not the salesman type and I try to keep things simple and provide fair and honest feedback.
). For those of you who know me, you know I am not the salesman type and I try to keep things simple and provide fair and honest feedback.
I have used many of the common forensic tools for many years now and can conduct keyword searches with the best of them (even in GREP ![]() ). I can also manually decode many of the common Internet-related artifacts that I may find or write an EnScript/Perl program to do it for me. But the reason why I have relied on IEF in the past is the simplicity and consistency in which it does exactly what I need. That is, search for Internet related artifacts and then let me quickly review those artifacts to see if they are relevant and need to be included in the investigation and provide me those artifacts in a form that I can either produce a succinct report or combine it with other relevant data.
). I can also manually decode many of the common Internet-related artifacts that I may find or write an EnScript/Perl program to do it for me. But the reason why I have relied on IEF in the past is the simplicity and consistency in which it does exactly what I need. That is, search for Internet related artifacts and then let me quickly review those artifacts to see if they are relevant and need to be included in the investigation and provide me those artifacts in a form that I can either produce a succinct report or combine it with other relevant data.
The simple answer is efficiency. I can certainly run a built-in automated process that is included with most existing forensic analysis tools, but none of them come close to the list of artifacts that IEF can find and more importantly can put that data in an easy to use form that does not require a bunch of munging to make it useful or play nice with other data that I may have from other sources.
There are some amazing things on the drawing board for future releases of IEF. But with that said, I really encourage you to provide any type of feedback (good or bad) about the product. The amazing team of developers at Magnet Forensics have some great ideas about new features for future releases, but we may not think of every possible way people use IEF, the data it produces or the way you want to use that data. If you have a suggestion, idea or complaint, please feel free to contact me anytime. My goal is to make myself available to help in whatever way I can. Even if you need assistance with using IEF with your investigation or just need information/something explained further, feel free to contact me anytime.
I can be reached at ‘lance (at) magnetforensics.com’ .

Using IEF v6′s New Timeline Feature To Reconstruct User Activity
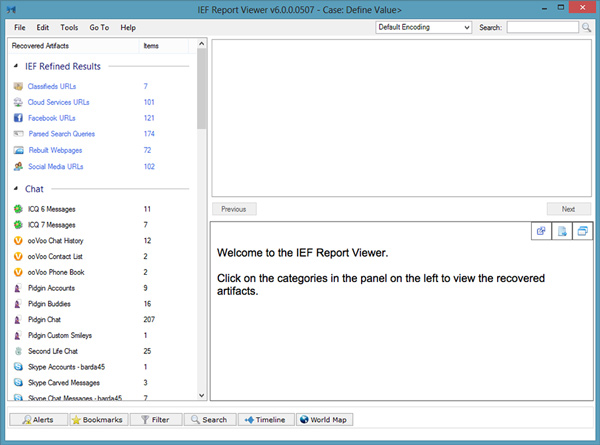
Welcome to Magnet Forensics’ newest IEF feature, IEF Timeline.
IEF Timeline provides a visual representation of your cases’ data. IEF Timeline allows you to move through time as events happen on a computer, allowing you to simply pinpoint activity at a particular point in time and easily cross reference the activity between artifacts. This can add a whole new dimension to your investigation, allowing you to reconstruct user activity and see events as they happened in chronological order.
You can open an IEF case in Timeline directly from IEF Report Viewer v6.0+ with just a single click, or launch IEF Timeline separately from the Start menu. IEF Timeline supports viewing IEF Cases, and TLN files (a standard timeline format).
When Timeline opens, you are greeted with two options; open an IEF Case, or open a TLN file.
Let’s go ahead and open an IEF case by selecting the case folder that you want to analyze.
Once you select a case, Timeline will begin processing the data and creating the timelines. If IEF Timeline is launched from report viewer it will automatically load the current case you are viewing.
When the artifacts are loaded, you are presented with a screen containing 3 defined sections: the Artifact List (1), the Timeline Overview (2), and the Main Timeline View (3).
(1) The Artifact List allows you to choose which timeline’s you would like to see in the main area. You can narrow your selection to just look at a specific artifact such as SkyDrive, a combined set of results such as IEF’s “Refined Results”, or simply everything in the case with the “All Results” tab.
(2) The Timeline Overview gives you a holistic view of the entire timespan of the data in the case. It allows you to adjust your visible region to a specific date, as well as panning and adjusting the current visible region.
(3) Finally we have the Timeline main area, which is a fully interactive playground of data. This is where you will see the spikes of internet activity.
Clicking on a time block, as seen above displays the set of events that occurred in that date/time range. You can select multiple blocks by holding down Control and clicking other blocks, or holding Control and dragging to select a range of blocks. In this particular case you can see that Google Drive was used to transfer the file ICQ.7z. Then, 2:38 minutes later, there was ICQ7 chat activity.
As you zoom in, the data becomes more granular, making it easy to pin point the events that happened between two times. There are multiple ways to zoom-in:
- Mouse wheel scrolling in on the main timeline area
- Use the zoom slider at the top right
- Shift + Click Drag to highlight a region to zoom-in to
- Use the grips on the sides of the visible region in the Timeline Overview to fine tune your visible region
You can navigate freely in all directions by clicking and dragging any lane the main timeline area.
You can export the selected data or all data in timeline to three different formats HTML, PDF, and TLN. More formats will be supported in future versions.
In combination with IEF Report Viewer, you have the ability to view Report Viewer’s bookmarks, search results, search alerts and filters in Timeline. You can simply switch views by selecting one of the databases in the dropdown at the top right.
TLN Format
The TLN format, defined by Harlan Carvey, is similar to a CSV file in the sense that values are separated, in this case by horizontal pipes ‘|’. In a TLN file, there are 5 values per line that follows the following format:
Time of Event | Location | Source | Artifact Name | Description
We hope that provides more detail on why IEF Timeline could assist you in your investigations and how to use it. Please feel free to contact us with any questions or suggestions, as always.
Thanks for your support!
Jad and the Magnet Team
// ]]>

Advanced Features of Internet Evidence Finder (IEF) v6
In this post, I want to go over a few of the new features that were introduced in IEF v6 that are subtle, but significant additions to IEF v6.
Jad recently explained the new powerful Timeline viewer that was introduced, so I will skip over that in this post.
Virtual Disk support
IEF v6 introduced parsing support of several common virtual disk structures. Now you can choose “Images” from the initial screen and point directly to a VMDK or VHD file just like an E01 or dd image.
IEF v6 even supports loading snapshot versions of VMDK disks.
DMG image and HFS+/HFSX file system support
IEF v6 can now natively load and parse DMG images, commonly used in the OSX environment. You can also now load image files that contain HFS+ and/or HFS+ file systems and IEF will parse them for all the supported artifacts just like an NTFS image.
Multi-core support
Time to break out the multi-core workhorses☺. IEF v6 now takes advantage of multi-core machines and significantly improves processing times. There is an option on the main menu that let you limit the number of cores IEF will use (default setting is to use up to eight, if available).


Network share support
IEF v6 now fully supports parsing data on remote storage that is accessible through a network SMB share. Any mapped or UNC path can be used to access remote files by selecting the initial “File/Folders” option.
You can even load administrative shares such as \\remotehost\c$ as long as you have the correct credentials to view the remote host’s administrative hidden share(s).
Auto-update feature
When used on a computer that has Internet access, IEF will now automatically check for updates upon startup and prompt you to download them, if available. For computers located in labs and secure locations, this “auto-check” can be turned off you (Tools->Auto-check) and you can download the latest version from the customer portal anytime.
As always, if you have any comments, suggestions or questions,
you can contact me directly at: lance (at) magnetforensics.com

More Encryption Detection Added to Free Tool Encrypted Disk Detector v2
A little while back Chad Tilbury, a SANS trainer and talented forensicator, was kind enough to write a blog post about our free tool EDD (Encrypted Disk Detector) and ask his readers to fill out a survey to indicate which additional encryption support they wanted added to EDD.
The response was great and made it easy to decide which encryption products to add support for. Today we are excited to release EDD v2 with improved encryption detection support for the already supported products (Truecrypt, Bitlocker, PGP, Safeboot), and added support for Checkpoint Endpoint Security FDE, Sophos Safeguard FDE, Symantec Endpoint Encryption FDE, and Bestcrypt. Other minor improvements were also added, including requiring the executable to run as Administrator (to ensure the tool doesn’t fail because it didn’t have Admin rights), and more intuitive colours for certain notifications (yellow = warning, red = encryption detected). Below is a screenshot showing EDD detect Symantec full disk encryption.
For those who are not familiar with EDD, it is a command line tool intended to be used on a live system that checks for full disk encryption or mounted encrypted volumes. The intention is that EDD is used when doing live response forensics to detect the presence of encryption before “pulling the plug” (and possibly losing all the data if the encryption password is not known). It takes a couple seconds to run so the process is not lengthy and it can easily be included in a batch file/script. Note that EDD does not search all files on the drive to detect entropy, it only looks for mounted encrypted volumes/FDE.
How does EDD detect the mounted encrypted volumes/FDE? Some of the FDE products out there leave a signature on the drive somewhere, either a volume boot sector or master boot record. The text/bytes they leave in places like that are helpful in identifying that the FDE product is present on the drive/volume, so those areas are checked by EDD. Some don’t leave these signatures, or the signature is only accessible when the hard drive is in an encrypted state (not helpful in a live scenario), so the best way to detect that they are running is to check for specific processes that are active when those FDE products are present. In some cases (when possible), we’ve implemented checks for both signatures and process detection in EDD v2.
EDD does not make any changes to drives or files on the live system, all of its operations are completed in a read-only mode. Running EDD is simple, simply run it without any parameters or use one of the below options when running in a script:
To download EDD, please click the link below.
If you have any questions , please don’t hesitate to contact us on our Magnet Support site.
Thanks for your support!
Jad and the Magnet Team

Magnet Forensics Recognized as One Of Canada’s Top Information & Communications (ICT) Technology Companies
Waterloo, Ont., April 23, 2013—Branham300 today ranked Magnet Forensics Inc. to its 20th annual list of the Next 50 Canadian ICT Companies, as ranked by revenue. The Branham300 list illustrates the depth and breadth of innovative technologies developed in Canada, and is widely considered to be a leading source of intelligence on Canada’s ICT industry.
Magnet Forensics, a global leader in the development of digital forensic software was also named to the Top 25 Up-and-Coming ICT Companies – a category ranked on innovation and promise.
‘Magnet Forensics is thrilled to be named to the Branham300 list in two different categories’, said CEO Adam Belsher. ‘This achievement is a testament to the strength of our flagship software, Internet Evidence Finder (IEF), and the dedication and focus of our talented team who continue to push the boundaries of innovation in our market.’
About Magnet Forensics Inc.
Magnet Forensics is a global leader in the development of software solutions for digital forensic professionals that assist them in building the best possible cases. Our flagship software, Internet Evidence Finder (IEF) was developed by a former police officer and forensic examiner who recognized the need for an easy to use, comprehensive tool to help perform digital investigations on digital media.
Since its creation, IEF has quickly become a trusted solution for thousands of digital forensics professionals in the world’s top law enforcement, government, military and corporate organizations in over 92 countries, used to recover a broad range of Internet-related communications. Court-admissible evidence recovered by IEF from computer hard drives and live memory can include webmail, browser history, social networking and cloud applications, P2P files and instant messaging communications; and has been used to support a wide-variety of investigations including cybercrimes, child exploitation, terrorism, human resource disputes, fraud, and intellectual property theft.
Media Contact:
Scott Williams, VP of Marketing, Magnet Forensics
scott.williams@magnetforensics.com
(519) 342-0195
About Branham Group Inc.
Branham Group Inc. (www.branhamgroup.com) is a leading industry analyst and strategic marketing consultancy, exclusively focused on the technology sector. Headquartered in Ottawa, Canada and with over twenty years of assisting global customers, Branham possesses a clear understanding of the major players and the market issues facing the technology industry. Branham conducts consulting work in the United States, Europe, Canada, Latin America, and Asia, providing the firm with a global market perspective. With a focus on creating value and roadmaps to success for the ‘Who’s Who’ in the industry and ‘Up and Coming’ companies, the company seeks to deliver market success to its customers.

Anecdotes from ADUC 2013
Last week was the 2013 Access Data User Conference (ADUC) in Las Vegas, and there were several hundred digital forensic professionals in attendance. There were several good presentations and speakers. Magnet Forensics had a booth there and I had the opportunity to meet many of the attendees. I spent several hours talking to digital examiners and asking questions about their current forensic workflow and for those already using Internet Evidence Finder (IEF), how and when they were implementing it during their investigations.
Not to my surprise, an overwhelming majority of the people I spoke to are using IEF concurrently with their favorite forensic analysis suite. Many are creating their forensic image(s), loading them in IEF and then letting it run while they simultaneously load the same evidence file into their forensic analysis weapon of choice and start their examination looking for non-Internet related artifacts. Almost all of the users expressed they preferred getting the comprehensive report from IEF rather than using the built-in artifact finding features of their forensic analysis suite.
One of the underlying questions was “when should I use IEF?” and/or “my case does not really involve social media, etc.” so I thought I would give a few thoughts on this:
Excluding strictly defined eDiscovery/litigation cases that limit your scope, almost every type of investigation has the potential of touching or recording some type of artifact type that is discoverable by Internet Evidence Finder. For example, Internet Explorer browsing history. Even if the case does not involve websites or Internet related activity, the fact that Internet Explorer records locally accessed files is reason enough to include parsing the Internet history files, at the minimum.
Whether the investigation is employee misconduct, fraud, theft, or intellectual property theft, the use of Internet-related technology is so pervasive in today’s business culture and personal life that it’s almost impossible these days not to leave some type of artifact somewhere.
It used to be said that a computer could be involved in an investigation one of three ways, although today, you could replace ‘computer’ with just about any personal digital device:
-
The digital device is the target of the activity
- i.e. unauthorized access, defacement, etc.
-
The digital device is the tool or method of committing the activity
- Web browser, chat, email, etc.
-
The digital device is a repository of information that may relate to the activity.
- The digital device was not involved at all, but it contains information that relates to the activity being investigated.
A good example of this is the recent arrest of a suspect allegedly involved in sending the toxic substance ricin to the President of the United States. The primary activity had nothing to do with Internet-related activity, although (as it’s been reported) the suspect used eBay to buy the necessary supplies to make ricin and he used PayPal to pay for it.
There are countless other cases where the initial activity/crime/investigation did not appear to be “computer” related at all, but yet communications, document, receipts or other relevant information is later found on a digital device.
So my answer to the original question is that except in rare circumstances where the scope of your examination is legally constricted, an examination of Internet-related artifacts is almost always a good initial step in every type of case. Like other investigative methods, let the artifacts lead you and provide a springboard to move to the next artifact (i.e. web history for PayPal, then identifying the account name, then getting records from PayPal).
As always, if you have any comments, suggestions or questions,
you can contact me directly at: lance (at) magnetforensics.com

Automating Internet Evidence Finder (IEF) with new CLI options in v6
Over the past few weeks, I have had several conversations with examiners and read a few message posts that voiced appreciation over the fact that Internet Evidence Finder (IEF) can read native evidence files (E01). Many of them explained that as part of their workflow after the acquisition/imaging process was complete, they would start Internet Evidence Finder and have it begin analyzing the evidence file while they simultaneously started examining the evidence using their favorite forensic analysis tool or using their time on other related tasks.
It’s no secret that I am a huge fan of automation (Why work harder when you can work smarter, right?). With the constant growth of hard drives and increasing size of data sets that often need to be examined during an investigation, I welcome anything that can ease the workload a bit. Starting with Internet Evidence Finder version 6.0.0.0507 (released May 15, 2013), there are some basic automation features available from the command line interface (CLI) that may be helpful during your workflow. I know many examiners who have developed custom scripts/batch files/utilities to “pre-process” evidence to extract the common artifacts and they don’t put “eyes on” the evidence until all the pre-processing is complete. It’s kind of like why wander around in the darkness trying to find what you need vs. let me generate a map first and let that drive where I go.
The main Internet Evidence Finder executable is IEF.EXE, typically located in the “C:\Program Files (x86)\Internet Evidence Finder v6\” folder. You can invoke this executable from the command line with no command line options and it will start the GUI. But if you pass some command line options, IEF will start in the command line interface (CLI) mode. To get some simple command line options, use “IEF.exe –h” (run the command prompt as Administrator or you will need to accept the UAC prompt):
Using the first example in the help information to search a single evidence file:
IEF.exe -i [image path] -s [type] -o [output path]
We can tell IEF to process a single evidence file (E01, dd, etc) by using the following syntax:
“ief -i "g:\Evidence Files\IEFDemoImage.E01" -s full -o “g:\IEF_Case”
This will spawn an instance of IEF in the background and it will process the evidence file using the “full” search option (all files, folders, unallocated, etc.) and create a case folder just like the GUI version does. You can then use the IEF Report Viewer to open up the case folder at any time later to review the artifacts that were found.
Alternatively, you can use a configuration file (undocumented beta in v6.0.0.0428) to specify the options you want to use while processing the evidence. Using the configuration file allows far more granularity in specifying what artifacts will be searched for as well as being able to specify some case information. Here is an example XML configuration file named “example.xml”:
The resulting case will look like this when opened in IEF Report Viewer:
You can use the config file with the following command:
IEF.exe --config “config.xml” --output “c:\case folder\ief”
Another advantage of using the config file is that you can specify multiple related sources (evidence files, file, drives, etc.) and IEF will process them consecutively and place all the artifacts found in a single IEF case file (db).
As always, if you have any comments, suggestions or questions,
you can contact me directly at: lance (at) magnetforensics.com

Internet Evidence Finder EnScript for EnCase v6 & v7
We recently added command line support to Internet Evidence Finder™ starting with version 6.0.0.0507 and briefly explained its usage in a post last week.
Since then, in an effort to try and make the workflow easier for examiners, we have been busy developing an Internet Evidence Finder EnScript for use with EnCase® v6 & v7. The goal of this EnScript is to make it easier for the examiner to launch an artifact search from within EnCase while they may be analyzing their case. IEF will run in the background and provide a familiar search status screen while it is searching and the examiner can continue working on their case in EnCase.
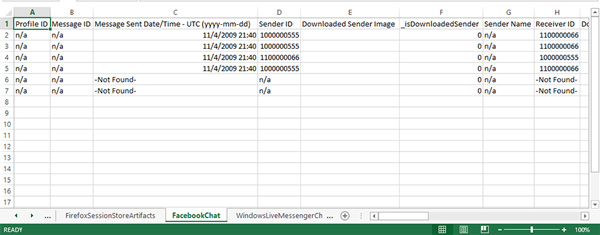
Once completed, the artifacts will be held in an IEF case file, just like if you had launched IEF the traditional way. In addition, once IEF has completed the search for artifacts, the EnScript provides the ability to copy the found artifact information back into EnCase as record data or into an Excel spreadsheet for additional review.
To install, simply copy the “Internet Evidence Finder.EnPack” to the appropriate folder, depending on the version of EnCase you are using. For EnCase v6 the typical location is:
C:\Program Files\EnCase6\EnScript\
or
C:\Program Files (x86)\EnCase6\EnScript\
For EnCase v7, the location typically is:
C:\Program Files\EnCase7\EnScript\
or
C:\Program Files (x86)\EnCase7\EnScript\
To run in EnCase v7, Choose “EnScript->Run” from to top menu bar, then select the EnScript (EnPack) you just copied into that folder.
For EnCase v6, double-click on the “Internet Evidence Finder” EnScript listed in the filter pane (lower-right).
Once the EnScript is run, you will be presented with the following dialog:
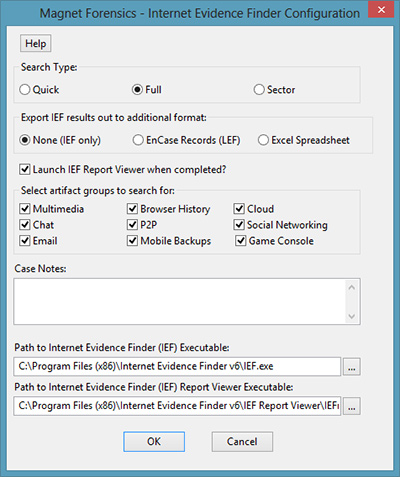
The first option equates to the “Search Type” option in IEF and defaults to “Full”. In the EnCase v7 EnScript, you are presented with three export options; None, EnCase Records or Excel Spreadsheet. These options do not exist in the EnCase v6 EnScript. “None” means the data found by IEF will be stored inside an IEF case file and can always be viewed by using IEF. The “EnCase Records” option means a copy of the found data will be exported from IEF and placed inside the EnCase Records tab for the current case. The last option of “Excel Spreadsheet” means a copy of the found data will be exported from IEF and placed inside an Excel Spreadsheet with each artifact type getting its own worksheet. The IEF case file and data are created and stored in the case’s default export folder.
The next option determines if you want the EnScript to automatically launch the IEF viewer and load the found artifacts so you can immediately review them in IEF.
The fourth option determines the types of artifacts you want IEF to search for.
Any text in the case notes is automatically transferred to IEF and entered into the IEF Case file. In addition, the examiner name and evidence number (EnCase v7) are automatically pulled from the EnCase case information when the case was initially created.
The final two options specify where the IEF.EXE and IEFRV.EXE files are. These two files are needed in order to launch IEF in the background and later load the case data, if selected. Once initially entered, this information remains each time you run the EnScript.
Once you click “OK”, you are presented with an evidence list where you can select which pieces of evidence you would like to process.
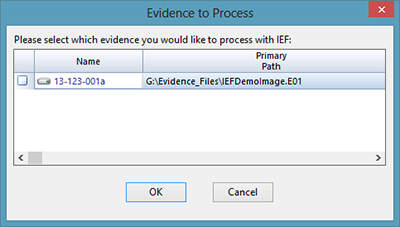
Once run, IEF will launch in the background and process all the evidence files you selected. An IEF status screen will be displayed:
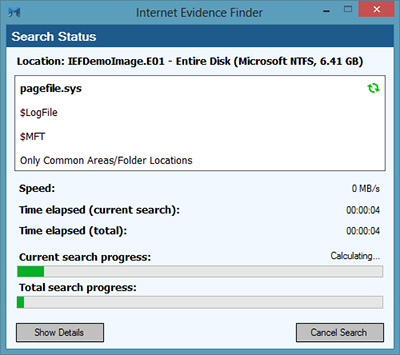
If you selected the option to have IEF Report Viewer launch, the case will be automatically loaded and displayed in the report viewed once complete.
If you chose the export option to have the data exported into EnCase Records, you will see this from the Evidence pane in EnCase v7:
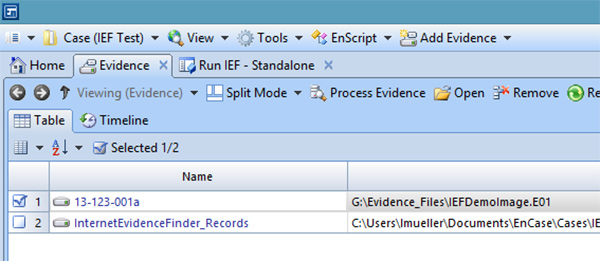
Clicking on that LEF will load the records in the records tab of EnCase:
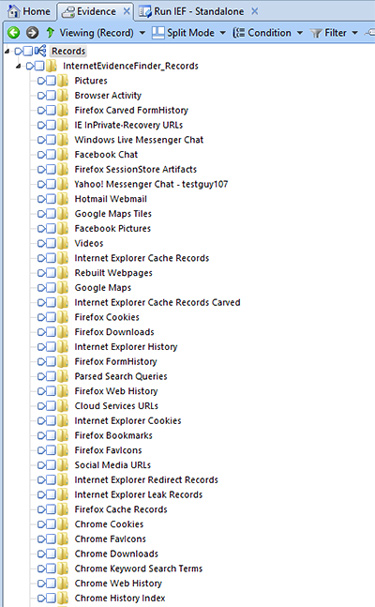
You can then view the found IEF artifact data the same way as you view other data stored in the EnCase Records structure and build custom filters/conditions to identify specific artifacts. You can always view the IEF data natively in IEF Report Viewer by double-clicking the IEFv6 case file stored in the default export folder of the case.
If you chose the “Excel Spreadsheet” export option, Excel (required) will automatically start and display the artifacts with each category of artifact on a separate worksheet. By default the XLS file is automatically saved in the default export folder of the case along with the IEF case file and other associated data.
As always, if you have any comments, suggestions or questions,
you can contact me directly at: lance (at) magnetforensics.com

Sneak Preview Into New Mobile Support In IEF – Come See Us At CEIC
Hello from CEIC in Orlando!
Over the past year we have been asked many times if we would consider adding support for recovery of Internet related artifacts on mobile devices. Our core competency is around the carving and parsing of Internet artifacts on computers so we decided to investigate further. We determined there are some great mobile phone imaging solutions but nothing that did a robust job of parsing and carving the deleted native phone applications (SMS, voice mail, contacts, etc.) and third party applications (social networking, chat, browser, and cloud).
After a great deal of research and development, we are pleased to announce that IEF will soon have support for recovering artifacts from mobile images/file system dumps and are confident that you will be as excited as us in what we are able to recover from mobile devices that have been factory reset or contain deleted data.
At CEIC 2013 we are previewing some of the features that will be available in the coming weeks.
Recover existing AND deleted SMS and voicemails from unallocated space:
Recover existing AND deleted Snapchat transfers/pictures, Skype and Whatsapp messages from unallocated space:
Recover existing AND deleted browser history, rebuild web pages from Safari and Chrome:
Support for iOS and Android based devices:
IEF has been a must-have computer forensics tool for many investigators and we are excited to extend our capabilities to assist you with your mobile investigations.
Please stop by booth #203 so we can show you a live demo and answer any questions you may have, or feel free to drop by just to say hello. It’s always a pleasure to meet new folks and our existing customers.
Thanks for your continued support!
Jad and the Magnet Team

Magnet Forensics is everything a start-up should be
The company is lean, produce incredibly strong revenue growth and grows by retaining earnings, not seeking investment. But what makes it stand out is that the company’s technology offers a massive benefit to society.

Canadian start-up hub thrives near Toronto
Twenty years ago, no one would have believed the Kitchener-Waterloo area would blossom into the most vibrant technology start-up community in Canada – the Silicon Valley of the North.
(Peter Moreira, Special for USA TODAY)

Mature Waterloo entrepreneurs defy tech industry age stereotyping

One of the most revered values in Silicon Valley is the notion that anyone with a great idea can become a success story. But it appears the work culture there is not as sunny as a typical California forecast.
Reuters reported in a feature series last November of age discrimination in the Bay Area’s tech community. Several older workers shared their struggles of losing out on opportunities to younger applicants and being perceived as incapable of keeping up with new technology.
In Ontario’s Waterloo Region, one of North America’s fastest growing startup clusters, stories like these can be worrisome for older entrants to the startup world.
However in the Waterloo tech cluster, a number of mature entrepreneurs have created successful new careers in tech, defying the industry’s ageist attitudes in the process.
(By Matthew Kang, CBC News)

Anecdotes from CEIC 2013
I just arrived back to California after spending this past week in Orlando, Florida for CEIC 2013. It was a good time and great to see so many familiar faces and finally put names to other faces who I had not previously met. Once of the best things about CEIC has always been the networking opportunities.
I first want to thank all the people that came by the Magnet Forensics booth and said “hello”. We had a great response from our existing customers as well as some huge interest from people who are new to Internet Evidence Finder (IEF). It is always great to hear the wonderful stories of how IEF has been used in cases and how it has helped either with a successful prosecution or simply to save time or improve the overall workflow. We always encourage people who are new to IEF to simply download a free trial and compare it to what they are currently using.
This year the founder and CTO, Jad Saliba was there as well as CEO Adam Belsher to meet and hear customer feedback. We are always striving to make IEF the best forensic tool it can be and we always appreciate hearing feedback on what features you like and/or want in the future.
Magnet Forensics also had several exciting announcements at CEIC this year, one of which was the announcement that IEF will soon be released (version 6.1) with mobile support!
This means the same easy to use GUI and options of IEF that you are familiar with can soon be used on a phone image or phone file dump.

The new version (released soon), will support Android and iOS based smartphones.

IEF with mobile will support parsing of most (if not all) the native clients application data. This means, SMS messages, call lists and contacts will be parsed if they exist AND carved from unallocated space. You can read about more of the features and original announcement here.
The second major announcement was about an EnCase v6 & v7 EnScript that we released to the public for free to help improve efficiency by allowing you to now run IEF from within EnCase and have the found artifacts brought back into EnCase (v7).

You can read about the detail of those EnScripts here. The EnCase v7 EnScript will be available on the EnCase AppCentral store soon.
We also announced last week that the latest version of IEF has added some API/CLI support for those of you that want to automate your evidence processing. It was great to hear reinforcing feedback from people at CEIC that they are beginning to think this way and build and automated workflow to process their evidence before an analyst even begins to look at the details of the data.
If we missed you at CEIC, we will be at the upcoming Techno Security & Mobile Forensics World 2013 conference in Myrtle Beach, SC on June 2-5, 2013.
As always, if you have any comments, suggestions or questions,
you can contact me directly at: lance (at) magnetforensics.com