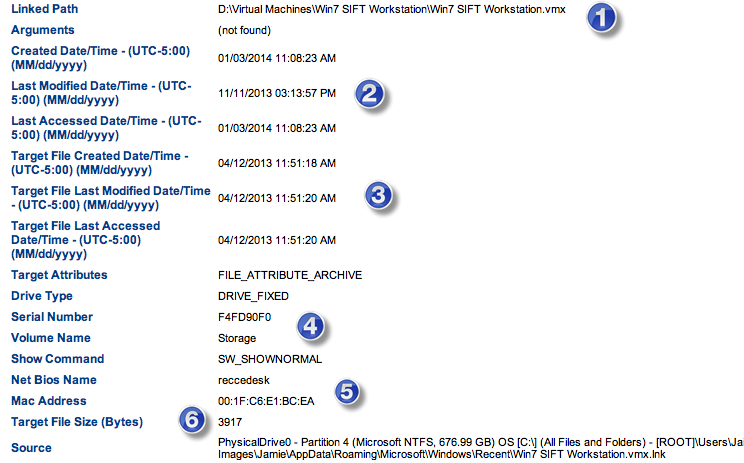
This is the second blog post in a series of six about the new features included in IEF v6.5
Investigations involving mobile devices have greatly increased over the past few years. In a recent blog series, we discussed how third-party mobile chat applications contain a wealth of evidence that can make or break your case. But over the last few months, a new type of social networking/chat application has emerged in popularity: the location-based mobile dating application.
Tinder, Grindr, Growlr and other apps that promote dating and meeting random people within your geographical area have become very popular with teens and young adults. Some call these applications geo-social networking apps, or lifestyle apps, and while they each have their own functions and features, typically these apps contain an element of IM/chat, picture and file sharing, and geolocation details to determine your proximity to the individuals you’re interacting with.
These apps were never intended to be used maliciously, but given their rise in popularity, they have made headlines around the world for facilitating dangerous situations:
Philadelphia police issue safety warnings to Grindr and Tinder users
Waukesha man arrested on suspicion of sex assault of 12-year-old
This post will touch on a few of the more popular location-based mobile dating apps, and will show you how to recover valuable data from these types of applications.
Tinder
Tinder is a very popular matchmaking app that uses your Facebook profile to present pictures and information about you to people within a specified radius of your current location (using your phone’s GPS). Users are presented with pictures of potential matches in their area and they can choose whether to swipe right and accept them as a match, or left to deny. If the other person also accepts you as a potential match, then you are able to start chatting.
Most people will agree that there are risks involved with meeting people online, especially when your location is included. Tinder does not provide your exact location, but it will list the distance of someone within your given radius. Forensically, if you’re ever tasked with examining a device with Tinder installed, there are a number of items that you can recover for your investigation.
Like many mobile applications, the majority of your data will be found in SQLite databases. For iOS devices the data can be found in Tinder2.sqlite at the following path:
Private\var\mobile\Applications\Library\Application Support\Tinder\Tinder2.sqlite
Similarly for Android devices, the SQLite database is called tinder.db and the path can be found below:
/data/data/com.tinder/databases/tinder.db
Both databases are similar in structure and will typically contain quite a bit of valuable data. There are a few tables in particular that you will want to investigate, including the messages, matches, photos, and users tables. The screenshot below shows how the tables and messages columns are sorted for an Android Tinder database.
![Blog 2 - Image 1]()
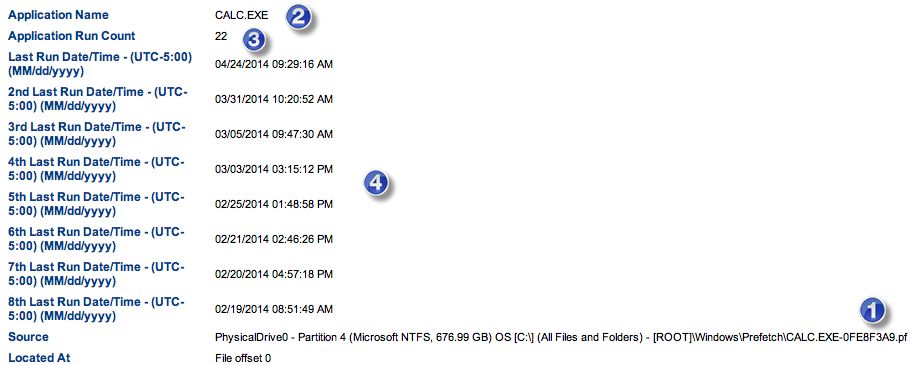
With the release of v6.5, IEF is now able to analyze Tinder artifacts for both iOS and Android devices. The four main categories of artifacts recovered are accounts, matches, messages, and photos.
![Blog 2 - Image 2]()
Account data will include details about the Tinder account owner including a unique user ID, a biography, birth date, distance (which is always 0 for the account owner), gender, first name and last activity date. Matches refer to anyone who has agreed to be a match with you (as described above). IEF will recover match data, including user ID, username, gender, creation and last activity timestamps, message count, any draft messages, and whether they have viewed your profile or not. Tinder messages are pretty straight forward and similar to any mobile chat application. IEF will provide the user ID, match ID, message contents, and message sent timestamps. Finally, IEF is also able to assist in recovering Tinder photos. The photos themselves are not stored on the local device, but they are stored online at images.gotinder.com. If your examination machine is connected to the internet, and you have enabled image downloading in IEF, the software will automatically download the Tinder photos to your case.
![Blog 2 - Image 3]()
Tinder is a widely popular app, but as with any social networking or matchmaking app, it contains a level of risk that user’s must be aware of. If you ever come across an investigation involving Tinder on either iOS or Android, IEF is an excellent tool to help recover the relevant data for examiners.
Grindr/Growlr
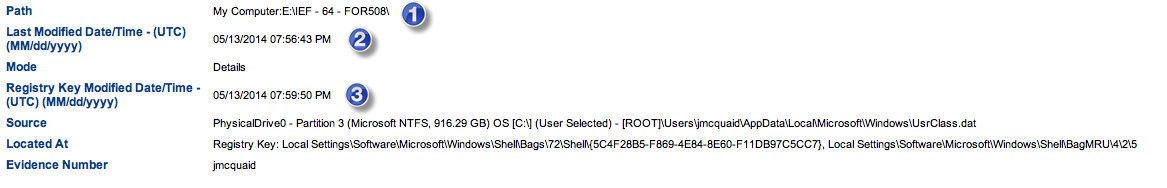
While popular, Tinder isn’t the only matchmaking application available on mobile devices. Grindr and Growlr are location-based apps similar in function to Tinder and other mobile dating applications, but are geared towards the gay and bi-sexual communities. Similar to Tinder, these apps promote meeting random people in your geographical area and can pose risk to the people who use them.
From a forensics standpoint, much of this data is stored in SQLite databases. Grindr and Growlr data can be found in the following locations for iOS and Android devices:
Grindr
iOS – /mobile/Applications/%GUID%/Documents/chatdb.sql
Android – /data/data/com.grindrapp.android/grindr.db
Growlr
iOS – /mobile/Applications/%GUID%/Documents/db.sqlite
Android – /data/data/com.initechapps.growlr/*.db (the database name is different based on user)
![Blog 2 - Image 4]()
IEF will recover the messages, buddies (contacts), notes, etc. for both Grindr and Growlr for iOS and Android devices. The results are organized for the examiner in a report that is easy to read and sort through.
![Blog 2 - Image 5]()
Both Grindr and Growlr are relatively easy apps to analyze, if you know where to look. The biggest challenge is building awareness amongst examiners so they understand how these apps operate and what evidence can be recovered.
Meet24
Meet24 is another location-based mobile dating and chat app rising in popularity amongst teens. Unlike the other apps discussed here, Meet24 does not use the SQLite databases to store its data. The app is a basic frontend for mobile browsers, meaning very little information is stored on the local device beyond some basic browser artifacts.
For Android, Meet24 will store some cached browser data at the following location:
/data/data/com.wildec.meet/cache/webviewCacheChromium
Support for this app was added to IEF v6.5 at the request of some of our law enforcement customers, who were investigating an increasing number of cases involving Meet24. IEF can retrieve cached pictures and website visits from acquired devices, but since much of the data for this app is stored directly on the Meet24 service, investigators may want to reach out the app developers directly to access additional data.
Snapchat
Snapchat is a photo and video sharing application allowing senders to define how long a recipient can view the message, before it disappears. While Snapchat isn’t necessarily a matchmaking or dating application, many users will often meet over Tinder and continue communicating through Snapchat or similar services. This allows users to send photos, or snaps, which will then disappear from a user’s device.
Unfortunately for the user, much of this data can be recovered from both iOS and Android devices. iOS will reveal only a limited amount of data, however when analyzing Snapchat artifacts on an Android device, examiners are able to recover quite a bit more data. The data is found at the following path:
/data/data/com.snapchat.android/databases/tcspahn.db and /cache/received_image_snaps/.
IEF is able to recover chat messages, logs, friends, pictures, videos, as well as a log of any snaps that were sent by the user.
![Blog 2 - Image 6]()
Looking a little closer, we are able to see a wealth of information from these Snapchat artifacts, including message contents, timestamps, sender, receiver, as well as a number of options and statuses for the message.
![Blog 2 - Image 7]()
Similarly, when looking at recovered pictures and video, Snapchat stores both the logs and images, which can be recovered. You will not always be able to recover the actual image but there should at least be a log of the activity found within the database. The extension for any pictures changes to .jpg.nomedia, but can still be easily recovered from the received_image_snaps path.
Due to the increased popularity of these mobile dating apps, it is quite likely forensic examiners will come across application data for Tinder, Grindr/Growlr, or Snapchat in their investigations. It is essential for anyone investigating these types of cases to be aware of the popular apps frequently used and the data that can be recovered. You can never be sure when a message, picture, or video recovered from one of these apps could be the deciding factor in your investigation.
Please let me know if you have any questions, suggestions or requests. I can be reached by email at jamie(dot)mcquaid(at)magnetforensics(dot)com.
Here are some related resources you might also be interested in:
- Read the next blog in our series: Recovering Live Systems Artifacts with IEF
- New to IEF: Request a 30-day trial
- Current customers: Upgrade to IEF v6.5
Jamie McQuaid
Forensics Consultant, Magnet Forensics
![]()














![Blog1_img1 [Image1]](http://www.magnetforensics.com/wp-content/uploads/2014/09/Blog1_img11.png)
![Blog1_img2 [Image 2]](http://www.magnetforensics.com/wp-content/uploads/2014/09/Blog1_img23.png)

![Blog1_img4 [Image 4]](http://www.magnetforensics.com/wp-content/uploads/2014/09/Blog1_img43.png)

![Blog3_img1 [Image1]](http://www.magnetforensics.com/wp-content/uploads/2014/09/Blog3_img1.png)
![Blog3_img2 [Image2]](http://www.magnetforensics.com/wp-content/uploads/2014/09/Blog3_img2.png)
![Blog3_img3 [Image3]](http://www.magnetforensics.com/wp-content/uploads/2014/09/Blog3_img3.png)






![Blog5_img1 [Image1]](http://www.magnetforensics.com/wp-content/uploads/2014/09/Blog5_img1.png)






























































