In our two recent webinars, “Using Technology to Find Information Faster and Build Stronger Cases” and “Finding the Best Starting Point for Insider Threats and Other Workplace Investigations”, members of our product management team described common practices and, specifically, how the latest Magnet AXIOM features offer investigators a defined process and appropriate detection/investigative techniques.
Attendees to both webinars asked a lot of great questions, and we wanted to take some time on the blog to go through and answer them.
The Basics
What RAM, CPU, and GPU specs do you recommend for a computer running AXIOM?
We recommend a CPU of 16 logical cores and 32 GB RAM. If you add cores to your CPU, plan to allocate at least 2 GB of RAM for every processing core in your system.
While it’s possible to run AXIOM on a basic system, with a CPU of 4 logical cores scan and 8 GB RAM, these minimum requirements might render poor imaging times in AXIOM Process, as well as slower actions in AXIOM Examine with larger data sets.
GPU support, meanwhile, was added for image classification in Magnet.AI as of AXIOM v2.2. Learn more in our blog post about the version here.
More information, including additional specs, is available on pages 13-14 in the AXIOM User Guide.
To optimize performance, what is the best hardware configuration?
There are a couple of different options to reduce any disk I/O bottlenecks:
- Run most active cases on a local SSD, and then store/archive completed ones on a RAID or external storage.
- Not required, but helpful to boost I/O, is to keep evidence images on one drive and your case on a separate drive.
Is it safe to open a case created with AXIOM 1.x in AXIOM 2.x?
AXIOM handles backwards compatibility for cases that were created on older versions of the software and opened in a newer version of AXIOM Examine.
Likewise, is it safe to open a case created with IEF in AXIOM?
The database structure for IEF is different from AXIOM, so you will need to reprocess an IEF case to open it in AXIOM.
Do you need a hardware write protect to make an image with AXIOM?
While it is not mandatory to use a hardware write blocker, it is certainly recommended as good forensic procedure. AXIOM should work seamlessly with most popular HW write blockers like Tableau, CRU, etc.
If I can’t remove the SSD from a laptop, what option do I have to examine the data in it using your tool or any other tool?
If you can’t remove the drive and you don’t have an adapter, you should plan to do either a live acquisition or boot disk to image the drive. (This is pretty common in Macs.) Jamie McQuaid, our Forensic Consultant, recommends Sumuri’s Recon Imager for this type of work, in addition to many Linux disks that will do similar things.
Loading and Working with Images in AXIOM
Can you add multiple images / pieces of evidence for multiple custodians? If yes, then how it will show under top artifact categories?
Yes, multiple forensic images or pieces of evidence can be added to Magnet AXIOM. They can be added in either a single initial scan, or more than one scan using the “Add New Evidence” post-processing workflow.
Following processing, each piece of evidence will be represented with its own unique evidence widget in the center column of the Case Dashboard.
Can you add or change images at any time, or only on the front end?
Evidence can be added to a case at any time. Removal is not currently possible, but is functionality we plan to add in a future release of Magnet AXIOM.
How do you bring in Oxygen and Cellebrite images?
Go to Mobile, select either iOS or Android as appropriate, then select “Load Evidence” and “Image”. Finally, select the forensic image you would like to load.
For a more detailed walkthrough of each process, see our blog posts:
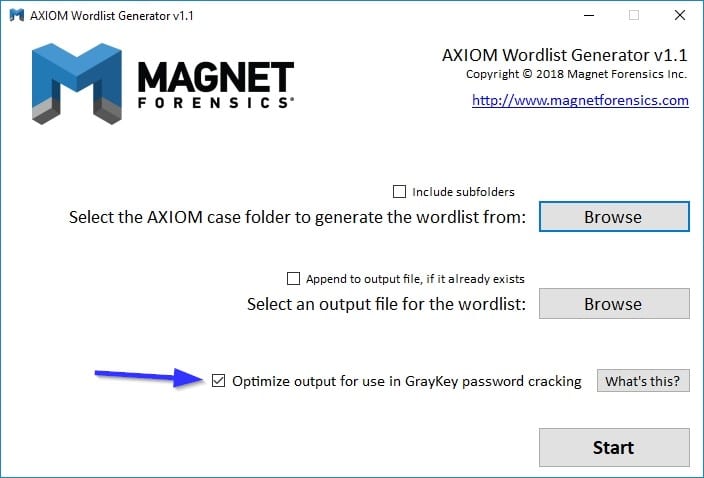
Will AXIOM process the keychains we get from GrayKey? If so, what’s the best way to import and view them? Can you use a keychain from GrayKey to attempt to identify possible passwords?
Yes, AXIOM will support the GrayKey keychain file. Be aware that this is slightly different than either a standard keychain plist, which is included in a regular iOS backup, or the keychain database found on jailbroken phones.
Working with AXIOM 2.0
Will the Volatility integration capture password hashes from memory?
We’ll include this in a new release of Magnet AXIOM coming soon.
Is there a de-duplicating function for documents and email?
AXIOM does de-duplicate documents and email, but our de-duplication focuses on artifacts recovered using a variety of techniques we employ during the image search. We currently do not de-duplicate documents and emails stored in different locations within the images.
Are PDF documents OCR’d during initial processing?
Not today, but optical character recognition (OCR) is functionality we plan to add to AXIOM this year.
Can the examiner select specific information from a database and bookmark it independently of the database?
Not today, but we also plan to add this functionality to AXIOM this year.
Is Bitlocker Recovery Key extraction supported in the memory analysis?
We’ll add this in a new release of Magnet AXIOM coming soon.
Where in Categorization can you select a level percentage of confidence match?
Magnet.AI currently filters categories by leveraging tags. We may look to add some additional flexibility around percent-based filtering in a future release.
Can AXIOM conduct malware analysis with the Volatility integration?
AXIOM will examine the host computer and memory for malware or other suspicious activity. However, it doesn’t do static or dynamic analysis on the malware you discover. The best practice, Jamie says, would be to export the malware out of AXIOM and use dedicated tools such as Cuckoo Sandbox, Ollydbg, or IDA Pro to actually analyze the malware.
How does Case Dashboard impact Portable Case?
At this time there is no impact, although we’re looking at extending the Case Dashboard to Portable Case. Most of all, we want to be sure to balance the presentation of good information that Portable Case currently provides, without overwhelming stakeholders with information.
The post How AXIOM Technology Helps Builds Stronger Cases from Start to Finish: Webinar Q&A appeared first on Magnet Forensics.