In this series, a few forensics experts within Magnet Forensics are sharing their suggestions for nominations in this year’s Forensic 4:cast Awards. In this first installment, Jessica Hyde, Director of Forensics, highlights people in the DFIR community who are making valuable contributions. You can submit your nominations (including Magnet AXIOM for DFIR Commercial Tool of the Year) here.
For those unfamiliar, every year, Lee Whitfield puts on the Forensic 4:cast awards. Lee does this as a community event with both a nomination and a voting phase. One of my favorite part about the nomination phase is that you can nominate as many folks, projects, tools, etc. as you want for any category! You can read the the rules and categories here.
Now, when it comes to final voting, you can only vote once—so that is where I lose sleep. The 4:cast awards are a great opportunity to recognize the people, teams, and organizations that have made amazing contributions to the community. But for now, you can nominate ALL THE THINGS here!
Magnet Forensics is providing an opportunity for some of us share our personal recommendations for nominations. I am so happy to do so. These are my personal nominations and not Magnet’s. Please note, I will not address every category, but just some of the ones where I would like to share around some people I have nominated and hopefully to inspire some of you to nominate as well or at least introduce you to sources, project, and forensic practitioners you may not know.
One of the most important things to note is that these nominations are for work done in 2018. This eliminates some really cool projects and work in 2019, like Eric Zimmerman’s KAPE tool, Blanche Lagny’s paper “Analysis of the AmCache”, and all of the resources put out by Joshua Hickman—both the blogs and the data sets . These are totally on my list for next year!
On to my suggestions for nominations this year! Please feel free to nominate these or share your thoughts. Just because someone isn’t listed here does not mean that I do not appreciate and love their work. Thank you all so much to your contributions to the community. I am a big proponent of sharing in DFIR. I can’t wait to see what the community brings in 2019!
DFIR Non-Commercial Tool of the Year
APOLLO by Sarah Edwards — As more examiners have access to full file system images, Sarah’s release of Apple Pattern of Life Lazy Outputer’er (APOLLO) which helps decode data from a variety of iOS databases including knowledgeC.db is an incredible tool for use on iOS cases. It has further capabilities to be used on devices outside of just iOS.
Volatility — With continued updates and plugins, this tool is totally indispensable for memory analysis. Memory analysis is a critical portion of forensic analysis and can be used to target your file system analysis, triage while still imaging, and recover artifacts that only live in memory.
DFIR Show of the Year
Forensic Lunch by David Cowen and Matt Seyer — The duo continues to bring the newest information to the community on a regular basis with both looks at tools and people who are contributing to the community.
Forensic Lunch Test Kitchen by David Cowen — David provides a look inside in-depth testing. This show has inspired the community to delve into further testing and understanding of artifacts and their creation. Forensic Test Kitchen is an amazing way to understand the methodology behind testing and validation and learn as a community. Thanks, Dave, for letting us inside your screen and head! It is the same link as the Forensic Lunch, so guessing that Lee may wrap these up as one.
Digital Forensic Survival Podcast (DFSP) — Every week Michael shares something with us that is useful. This could be anything from a deep dive into a specific artifact to a digital forensic technique. If you aren’t listening, you should! New episodes come out every week.
DFIR Blog of the Year
Initialization Vectors by Alexis Brignoni — Alexis drafted 33 posts, mostly related to mobile device forensics, throughout the year. Many of these prove critical to investigations and have associated scripts that were highly usable for forensic examiners.
ThisWeekIn4n6 by Phill Moore — This blog lets the community know what other blogs we should be reading this week and all of the critical information we need in the ever-changing landscape of digital forensics. I regularly use this cite as a reference to find past articles on topics. How Phill is able to find everything, I will never know.
HECFBlog by David Cowen — David contributed nearly a blog a day for the entirety of 2018. In addition to the continual daily posts, this blog encouraged the community to do further testing through Sunday Funday challenges and sharing of the results. This spawned other forensic practitioners to create their own blogs in response to the challenges.
DFIR Book of the Year
SQLIte Forensics by Paul Sanderson — This is everything you want to know about SQLite and how to conduct forensics on the data within. This is indispensable for mobile investigations as there are so many SQLite dbs across Android and iOS that regularly need to be parsed by the examiner because the applications are not supported by commercial tools.
Investigating Windows Systems by Harlan Carvey — Harlan’s book allows the user to get inside the mind of an investigator and understand more than just the data that lives in a registry key or an artifact from a file system, but the methodology behind how an examiner analyzes evidence and pivots throughout the investigation.
DFIR Article of the Year
“A forensic examination of the technical and legal challenges surrounding the investigation of child abuse on live streaming platforms: A case study on Periscope” by Graeme Horsman — This paper discusses both the issues with forensic investigations of streaming platforms as well as methodologies. This is critical work as we move forward.
DFIR Social Media Contributor of the Year
Brett Shavers – Brett not only shares a slew of material that he creates, but also discusses and amplifies messages from the community. He regularly provides context to the information shared by others.
Jake Williams (aka Malware Jake) — Jake’s brand of sharing on social media is unmatched in both true discussion of current events that impact our field and in terms of clever depiction of animal videos as they pertain to information security. Jake is not afraid to have a real discussion full of unpopular opinions to ensure that the truth is illuminated.
DFIR Undergrad, Graduate, or Training Class of the Year
SANS FOR 518 by Sarah Edwards — I took this class in 2018 and was amazed by the sheer amount of knowledge that was bestowed. She updated the course to reflect the changes in APFS and ensured that the practical was valuable. Walking out of that class you have skills that can be used for a lifetime.
DFIR Groundbreaking Research of the Year
Grayshift — The development of GrayKey allows for Law Enforcement to have access to parts of iOS devices that has not been seen since the Boot Rom Vulnerability days. This has been truly groundbreaking work that has provided access to data to a variety of devices unseen.
Maxim Suhanov — Maxim has done an unprecedented amount of research in 2018. This includes everything from work on Last Access timestamps in NTFS to deep registry analysis. His work has been truly groundbreaking in the field.
Steve Watson and crew of VTO Labs — Steve Watson and his team did incredible research surrounding Drone Forensics. They released over 20 reports on the forensic analysis of drones including releasing drone images on the NIST CFReDS page. This allows examiners to have access to images from drones for creating parsers and to understand the kinds of data that is stored from drones and how it could be recovered.
DFIR Newcomer of the Year
(Treating this category as people who began sharing in 2018 – not necessarily new to the field)
Kevin Murphy — Kevin created and contributed the open source Manta Ray project which is a hash set from Virus Share so tools could incorporate those hash sets for rapid identification.
Delaney Jester — Delaney is new to the scene, but still put out a blog about her research regarding Forensics of Cortana on Android this summer.
Kevin Pagano — Kevin, although not new to forensics, started a blog in 2018 where he shared forensic information on everything from TeraCopy forensics to summaries of forensic conferences. I am really looking forward to what he has to bring in 2019—he already has done amazing in both winning two forensic CTFs (BloomCon and Magnet User Summit – in the same week!) and competing in the Sunday Funday Challenges put out by David Cowen at Hacking Exposed Computer Forensics Blog.
DFIR Resource of the Year
This Week in 4n6 by Phill Moore — Go-to website for understanding all the information the forensic community puts out each week. Additionally, it serves as a source in order to be able to find articles about topics that you know you read but don’t recall where they were. Serves as the forensic index of sorts.
DFIRTraining by Brett Shavers — This is the source of sources. This site has been updated greatly this year to include not only Tools and Training, but variety of resources from books, to artifacts, to education. It is the resource of resources!
AboutDFIR by Devon Ackerman and Mary Ellen Kennel — Fantastic resource that has added amazing sections this year including the DFIR Jobs section and the Research section. Newer forensicators have been inspired by the research section to take on new projects and share.
DFIR Team of the Year
Cyber-investigation Analysis Standard Expression (CASE) Consortium
— CASE is a community that intersects academia, governments, non-profits, and commercial vendors to create a standard for expressing the output of forensic tools such that in the future data from one tool will be able to be exported, ingested, and shared using the same definition of traces. This will help the entire community as it will allow for data from multiple tools to be correlated and collated as well as allow for transference of data while maintaining its provenance.
Steve Watson and the team at VTO labs — Steve has been leading many revolutionary projects at VTO Labs. This includes information not only drone research and information which the team has put out, but also research surrounding IoT devices where he brought together the community in Data Finder events throughout the year to research together and document their findings. Additionally, VTO labs has explored how to recover data from damaged devices, including using water samples from around the world and producing techniques as to how to recover data. The team also has researched biohazards around digital forensic evidence of unknown origins and crime scenes and the wearing of proper Personal Protective Equipment (PPE) to protect digital forensics practitioners.
Digital Forensic
Investigator of the Year
Alexis Brignoni — Alexis has worked tirelessly to share information he learns from his work and to share information and tools with the community via his blog, scripts, and putting his scripts into formats for automatic ingestion by commercial tools. He has also mentored new forensic practitioners, worked with peer investigators around the world when asked to help in their investigations, and released tools and methods that are critical to examiners. He has translated content into other languages so that examiners could have access to posts not in their language. Alexis is an extraordinary examiner and person who does both cutting edge research, mentors, and finds ways to give back to the community at every opportunity.
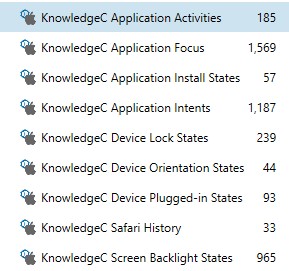
Sarah Edwards — Sarah continues to rock putting out information about iOS and Mac forensics. She helped us all understand APFS, released APOLLO, taught examiners how to get file system acquisitions from jailbroken phones, updated the FOR518 class, and shared a whole litany of goodies about KnowledgeC with us over the month of December on her mac4n6 blog.
David Cowen — David is the epitome of the ultimate forensic teacher and mentor. He has encouraged the entire industry to do and share more with the Sunday Funday challenges. That has led to multiple examiners sharing their dives into specific artifacts and forensic analysis. In addition, he put on two CTFs for the community, plus his daily blog, and introduced the Forensic Test Kitchen above. David contributes in one of the most fantastic ways, not only does he share the knowledge he has gained but challenges the rest of the community to be better and share what they learn and test. He even shows us how to think out of the box and test to become better examiners. Thank you for making us all better as a community, Dave!
Phill Moore — Most forensic aficionados are aware Phill contributes weekly via thisweekin4n6, but what some may not know is that he doesn’t just compile and interpret the rest of the community’s findings, he also shares his own. Phill has a blog full of his research at https://thinkdfir.com/. In addition to both of his blogs, Phill also does a monthly podcast, This Month in 4n6. Additionally, he released several scripts this year at https://github.com/randomaccess3, including one for querying Google Home devices.
Yogesh Khatri — Yogesh has released a slew of information this year on his blog https://www.swiftforensics.com/. One of the things I really appreciate about Yogesh is that he dives deep into both Mac and Windows forensics and is incredibly knowledgeable in both sides of the house. He posted 8 blog posts this year and multiple scripts. He is the author of the mac_apt project which is incredible. His downloads can be found here: https://www.swiftforensics.com/p/downloads.html
Brett Shavers — Brett shares a massive amount of information and perspective. He does this in a variety of ways through his own blog – https://brettshavers.com/ where he breaks down forensic life for real, as well as through dfir.training mentioned above. In addition, Brett has created a variety of downloadable courses on his website. Brett also does several case study releases to his Patreon supporters. Brett has a knack for making forensics relatable through his wide array of experiences and explanations.
Dr. Eoghan Casey — Many know Eoghan for his book “Handbook of Digital Forensics and Investigation”; however, Eoghan has made significant contributions to our community this year. Eoghan continues to contribute through his academic publications and teaching of students. Additionally, he contributes to the community in so many other ways. He has been the leader of the Cyber Analysis Standard Expression (CASE) movement described earlier. He regularly contributes critical research to a multitude of journals. He is the editor in chief of Digital Investigation journal. He also oversees the Forensic Challenge that DFRWS puts out including the challenge last year around IoT devices. Eoghan has been critical in the DFIR Review project (although that is a 2019 submission) allowing for peer review of practitioner created blogs. In addition to these multitude of creations – he works with Cyber Sleuths Labs to bring digital forensic education to 9-12th grade women and other underrepresented groups through digital forensic exercises and summer camps. Thank you, Eoghan, for all your contributions to enriching the community and bringing together future generation of examiners, academia, and practitioners.
Well those are my picks! Thanks for reading. Most importantly, if you haven’t done so yet,
please head over to https://forensic4cast.com/forensic-4cast-awards/2019-awards/
and nominate any and all examiners, projects, tools, blogs, podcasts, etc. that
you feel are worth recognizing. There is too much in forensics for anyone to
have a grip on everything and I am eternally grateful to all of the people
mentioned here for their contributions to our community.
If you have any comments or
questions feel free to reach out to me at Jessica.hyde@magnetforensics.com.
The post Who We’re Nominating for This Year’s Forensic 4:cast Awards: Part 1 appeared first on Magnet Forensics.
 By Jessica Hyde, Director, Forensics
By Jessica Hyde, Director, Forensics