We’re proud to announce the availability of Magnet AXIOM 4.0!
Magnet AXIOM 4.0 and an updated Magnet AXIOM Cyber are now available to download within AXIOM or over at the Customer Portal. With this next step in AXIOM’s evolution, we’ve brought huge enhancements to the speed, flexibility, and reliability of AXIOM. And with AXIOM Cyber, we’re excited to introduce remote collection of Macs and Azure virtual machine image acquisitions.
If you haven’t tried AXIOM or AXIOM Cyber yet, request a free trial here.
Up to 5X Faster Filtering
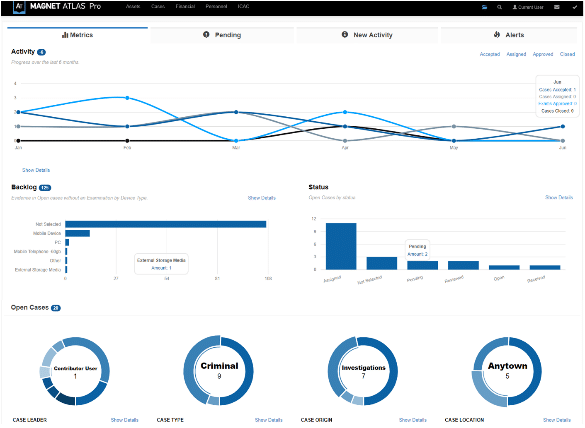
We’ve dramatically reduced the amount of time it takes to filter data compared to previous versions of AXIOM. Now, searching and filtering can happen up to 5x faster, depending on the size of the case and the data set returned from your search—reducing your downtime and helping you get your cases completed even faster.
See for yourself how AXIOM is reducing filtering time in this blog from Tarah Melton.
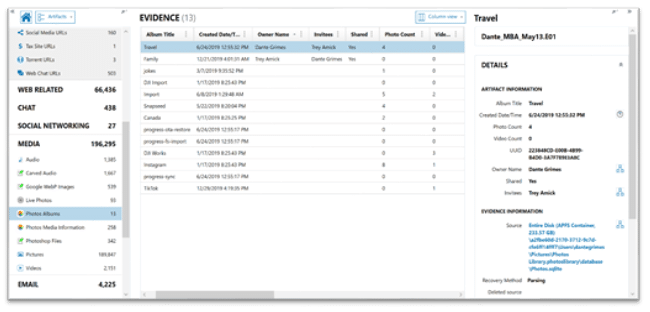
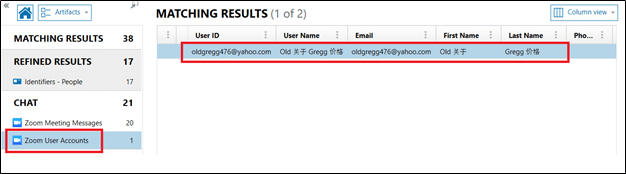
Find Similar Pictures
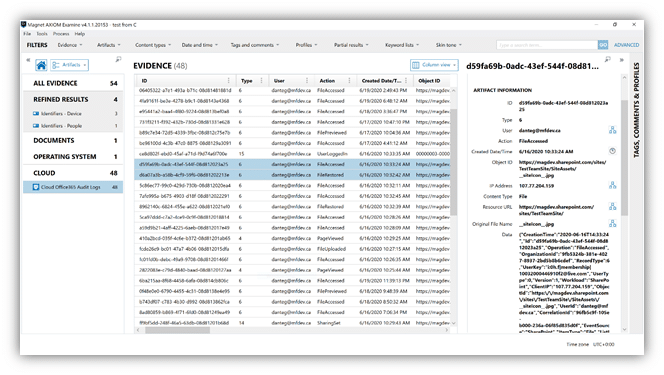
Using integrated CBIR (content-based image retrieval), AXIOM can automatically locate pictures containing similar features. Examples include pictures with similar subject matter or pictures that were taken in the same location as a part of a series. From there, pictures are displayed in ranked order based on similarity to the query picture in the thumbnail view.
Once the ‘Build Picture Comparison’ process is completed, you can right click on any image in your case and select ‘Find Similar Pictures’ to see the results. The ‘Build Picture Comparison’ task can be run manually, or automatically when the case processing has been completed.
You’ll also be able to load external pictures that aren’t in your case to find similar pictures within the case file by selecting ‘Import picture to find similar pictures’ from the Tools menu. The imported image is only used as a reference and is not included in the case file.
See it in action in this blog and how-to video from Trey Amick.
Reimagined Exports
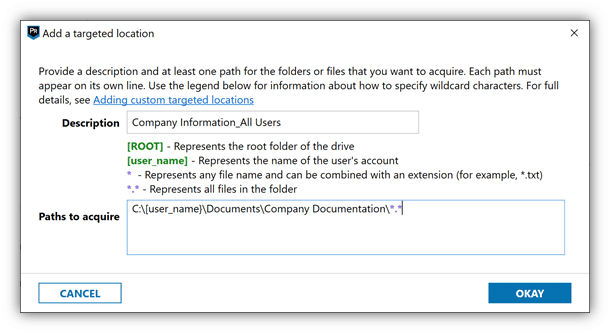
Reporting is easier than ever with customized Exports. Now, you can choose to include only data relevant to your case such as specific artifact types and columns.
And with the new addition of Export Templates for similar case types, efficiency and consistency of exports is improved—with standard formats agency-wide helping to streamline processes. It’s easier than ever to export and import these templates and share them with your colleagues.
Learn more in this blog and video from Tarah Melton.
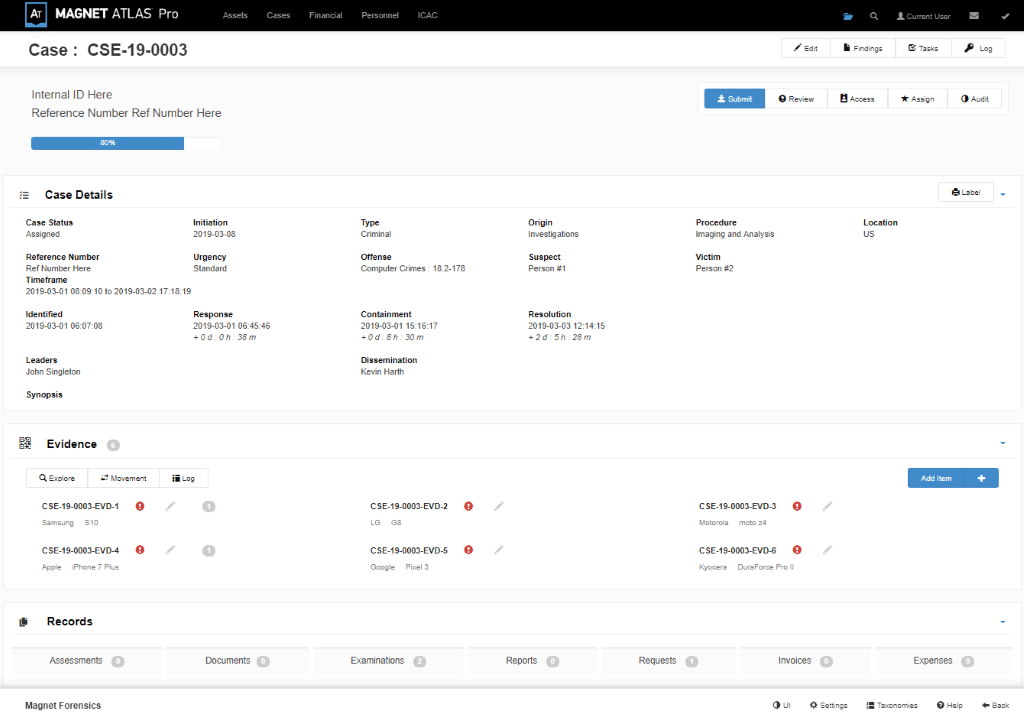
Stronger Reliability with Scan Summary and Exception Reporting
Thanks to a new detailed Scan Summary and Exception Reporting, you can improve the defensibility and reproducibility of examinations by knowing what data was scanned and what may have been missed.
Now, if you have multiple evidence sources scanned and one fails, you can use the new details pane to understand what needs to be re-scanned and what likely caused that outcome.
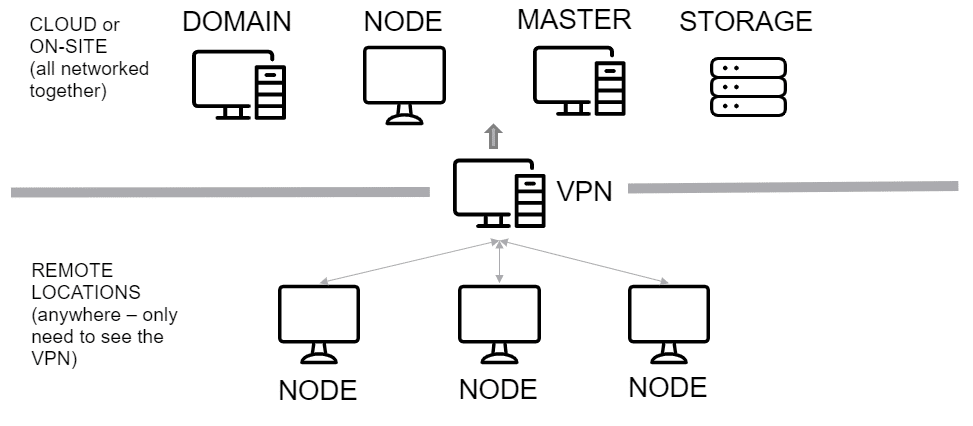
New in Magnet AXIOM Cyber: Remote Collection From Macs
With Magnet AXIOM Cyber, you can remotely browse and reliably acquire files from Macs without having physical access. That includes remote collections from Macs with T2 security chip encryption or System Integrity Protection enabled.
AXIOM Cyber makes it even easier to use one tool to remotely collect data from Macs and Windows devices and then analyze it alongside data from computer, cloud, and mobile evidence sources in a single case file.
Azure Virtual Machine Acquisitions Now in AXIOM Cyber
Use AXIOM Cyber to acquire virtual machine images hosted in Microsoft Azure as a part of your investigation. AXIOM will then automatically begin processing the VM image once it has been acquired to simplify the workflow.
The acquired image is a .VHD which represents the virtual hard drive of the virtual machine running in Azure.
This feature requires advanced configuration of the Azure environment to provision an account that has permission to image VMs.
New Artifacts
- Albums — Photos (macOS)
- Houseparty (iOS, Android)
- iCloud Local Files (macOS)
- ID for Advertisers (iOS)
- KnowledgeC – App Usage (macOS)
- KnowledgeC – App WebUsage (macOS)
- LogMeIn Activity (Windows)
- Private Photo Vault (iOS)
- Safari Preferences (macOS)
- TeamViewer File Transfers (Windows)
- TeamViewer Sessions (Windows)
- Wickr (Android)
- Z shell (macOS)
Updated Artifacts
- Albums (iOS)
- Android 10 System Artifacts (Android)
- Apple Notes – Voice (macOS and iOS)
- Cached Locations (iOS)
- Chrome Logins
- Chrome/Webkit Browsers (Android)
- Live Photos (macOS)
- Mail (iOS)
- Messenger (iOS)
- OS Information (macOS)
- Outlook (macOS and Android)
- Safari (iOS, macOS)
- TextFree (iOS)
- Threema (iOS)
- Twitter (iOS)
- Videos (macOS and Windows)
- VK (iOS)
- Wickr (iOS)
- Zalo (iOS)
- Zoom (Android, iOS)
Get Magnet AXIOM 4.0 Today!
If you’re already using AXIOM or AXIOM Cyber, download AXIOM 4.0 over at the Customer Portal. If you want to see how AXIOM 4.0 can help you find the evidence that matters, or how AXIOM Cyber can help you simplify remote acquisitions, request a free trial today!
The post Faster. Flexible. Trusted. Magnet AXIOM 4.0 is the Strongest Version of AXIOM Yet appeared first on Magnet Forensics.