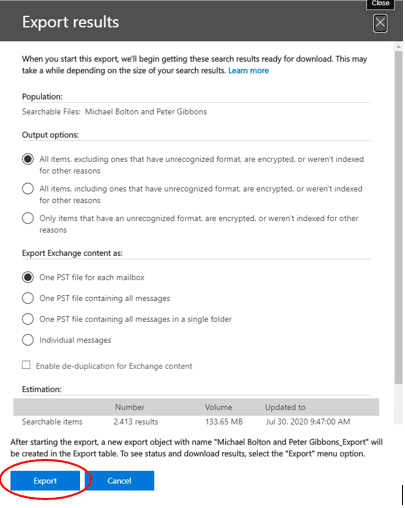
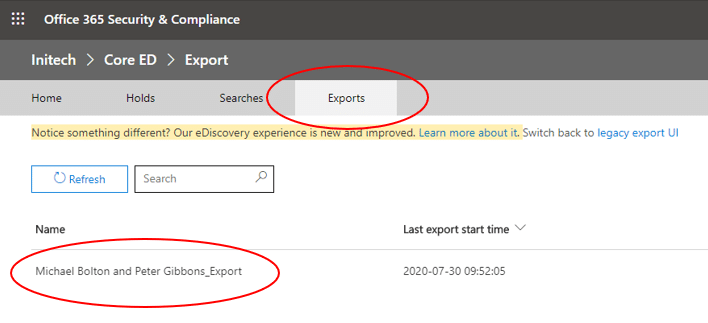
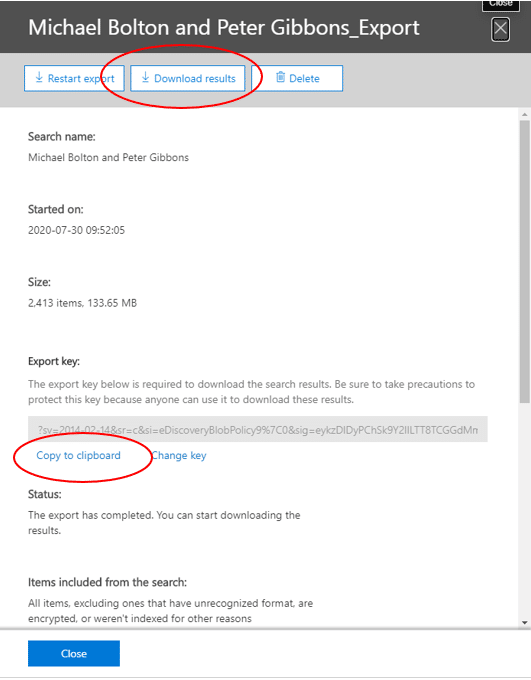
Hi! Jessica Hyde here with Kevin Brightwell, Senior Software Developer, and the technical lead for our integration of AFF4 and AFF4L.
In AXIOM 4.2, we have integrated AFF4 support for forensic images and we wanted to take an opportunity to share how we believe this integration and further acceptance of the AFF4 and AFF4-L formats can be of benefit to the forensic community.
What is AFF4?
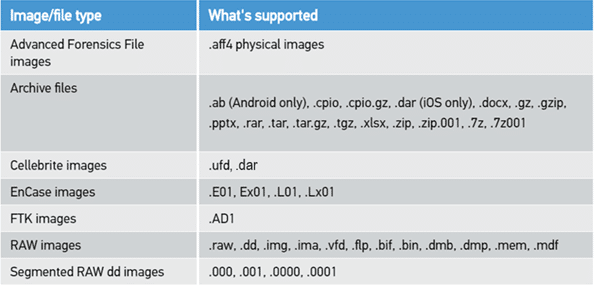
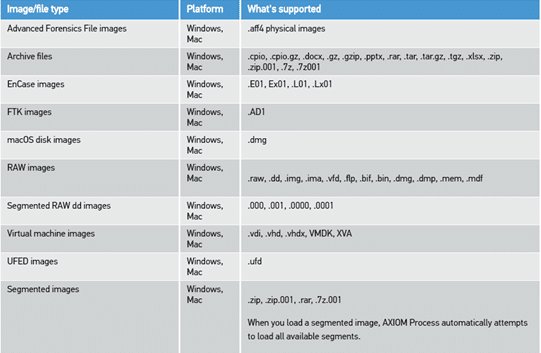
AFF4 is a forensic container that allows for creation of forensic images. The format was created in 2009 and explored in the paper “Extending the advanced forensic format to accommodate multiple data sources, logical, evidence, arbitrary information and forensic workflow” by Michael Cohen, Simson Garfinkel, and Bradley Schatz. Documentation, and overview and GitHub repository for the project can be found at http://www2.aff4.org/. AFF4 is not that new, but it provides some distinct advantages over other forensic containers.
One of the most touted features of AFF4 is the increased imaging speed. AFF4 utilizes block hashing as its primary hash validation. This is a major advantage in time as it allows the image to be verified while it is being opened. Linear hash verification is still available if a lab requires it; however, it is now possible for labs to utilize block hashing to validate the image integrity initially and delay or eliminate potentially lengthy linear hash verification until after processing – getting you to your results faster.
In addition to speed and block-hashing, there is another critical feature of AFF4. The format is open source and vendor neutral as opposed to proprietary formats such as .E01. There is a vibrant community that works on the format and it has been peer-reviewed through numerous academic papers published in peer-reviewed journals. Several academic references are listed at the end of this post.
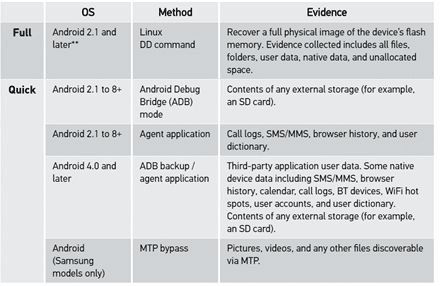
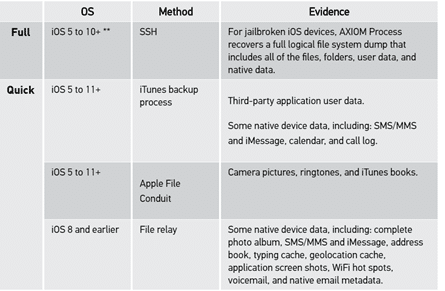
AXIOM began supporting AFF4 physical images from MacQuisition in version 3.7. Starting with the release of AXIOM 4.2 we will be supporting AFF4 images from other sources like Evimetry. Other imaging platforms that support creation the of AFF4 include Atola TaskForce. These are commonly seen as two of the fastest imaging platforms on the market.
AFF4-L
What about logical images? The current “standard” format of today is the proprietary .L01 format. There is no public specification for this format and hence it cannot be updated to meet new needs as evidence evolves. This is where AFF4-L comes in. AFF4-L is a new open-source, vendor neutral standard for logical images that is based on the AFF4 format.
There are several areas where the community would benefit using AFF4-L. This includes acquisitions from the cloud, targeted acquisitions, and exports of subsets of data. Cloud acquisitions tend to take the form of data streams, often in JSON, that need to be stored in some container. Targeted acquisitions often contain raw files from specific destinations on a remote or attached system. In other instances, examiners need to deliver a subset of data to another examiner or organization for a variety of reasons including keeping the exam to a scoped set of data, sharing of only responsive data, and the redaction of contents that are not sharable with another organization due to confidentiality or other reasons. The ability to store contents in these circumstances in a forensics container in a vendor agnostic, non-proprietary forensic format is critical.
Today, these exports are typically done in either archive formats like .zip, .rar, or .tar. These exports can be problematic. For example, when data is exported in a zip and moved to another system, the MAC times on the folders may change. Now this can be overcome using a log file that contains metadata regarding the initial contents of the file. However, there is value in having a true forensic container to ensure integrity of the contents.
Additionally, the AFF4-L format has potential to be used when contents are exported to be shared with other parties like counsel. This would allow for the contents to maintain forensic integrity. As a vendor-neutral, open source standard, this format can also serve as a method of sharing and moving data between different tools.
There are potential other uses for the AFF4-L format. Some other uses can include serving as a forensic container for logical mobile images. Use of an open standard for imaging of mobile devices will allow for those forensic images to be used in multiple tools instead of only being processed by the tool that created a proprietary image type. Additionally, the AFF4-L format could potentially be used with Load files in the future for providing data to eDiscovery platforms.
The Format of the Future?
There is a great need by the forensic community to utilize an open-source container for forensic images such as AFF4 for physical images and AFF4-L for logical images. Use of the AFF4 and AFF4-L formats has the potential to increase the interoperability of tools. The image format is created and improved upon with community input and has been peer-reviewed by academia. The format is feature rich and easy to read. Because AFF4 and AFF4-L utilize plain-text TTL (.turtle) files, the contents of a hierarchical file system can be navigated by a human, not just a machine. Most importantly AFF4 and AFF4-L provide strong fast integrity verification.
Now is the time for the forensic community to begin wide acceptance of this open-source, non-proprietary format that is tested, validated, peer-reviewed open to anyone for both physical acquisition and logical images and exports.
Please feel free to reach out to us, jessica.hyde@magnetforensics.com or kevin.brightwell@magnetforensics.com with your comments or questions about our AFF4 integration or our thoughts on the future of AFF4-L. We would love to hear your thoughts.
AFF4 and AFF4-L references
Cohen, M., & Schatz, B. (2010). Hash based disk imaging using AFF4. Digital Investigation, 7. doi:10.1016/j.diin.2010.05.015
Schatz, B. L. (2019). AFF4-L: A Scalable Open Logical Evidence Container. Digital Investigation, 29. doi:10.1016/j.diin.2019.04.016
Cohen, M., Garfinkel, S., & Schatz, B. (2009). Extending the advanced forensic format to accommodate multiple data sources, logical evidence, arbitrary information and forensic workflow. Digital Investigation, 6. doi:10.1016/j.diin.2009.06.010
Schatz, B. L. (2015). Wirespeed: Extending the AFF4 forensic container format for scalable acquisition and live analysis. Digital Investigation, 14. doi:10.1016/j.diin.2015.05.016
Schatz, B., & Cohen, M. (2010). Refining Evidence Containers for Provenance and Accurate Data Representation. Advances in Digital Forensics VI IFIP Advances in Information and Communication Technology, 227-242. doi:10.1007/978-3-642-15506-2_16
Shatz, B. (2015). U.S. Patent No. US10354062B2. Washington, DC: U.S. Patent and Trademark Office. Aff4. (n.d.). Aff4/Standard. Retrieved June 26, 2020, from https://github.com/aff4/Standard
The post AFF4 & AFF4-L — An Open Standard for Forensic Imaging appeared first on Magnet Forensics.